Software program firm Retool says the accounts of 27 cloud clients have been compromised following a focused and multi-stage social engineering assault.
Retool’s improvement platform is used to construct enterprise software program by corporations starting from startups to Fortune 500 enterprises, together with Amazon, Mercedes-Benz, DoorDash, NBC, Stripe, and Lyft.
Snir Kodesh, Retool’s head of engineering, revealed that each one hijacked accounts belong to clients within the cryptocurrency business.
The breach occurred on August 27, after the attackers bypassed a number of safety controls utilizing SMS phishing and social engineering to compromise an IT worker’s Okta account.
The assault used a URL impersonating Retool’s inner id portal and was launched throughout a beforehand introduced migration of logins to Okta.
Whereas many of the focused staff ignored the phishing textual content message, one clicked the embedded phishing hyperlink that redirected to a faux login portal with a multi-factor authentication (MFA) type.
After signing in, the attacker deepfaked an worker’s voice and known as the focused IT staff member, tricking them into offering a further MFA code, which allowed the addition of an attacker-controlled machine to the focused worker’s Okta account.
Hack blamed on new Google Authenticator sync function
Retool is blaming the success of the hack on a brand new function in Google Authenticator that enables customers to synchronize their 2FA codes with their Google account.
This has been a long-requested function, as now you can use your Google Authenticator 2FA codes on a number of gadgets, so long as they’re all logged into the identical account.
Nonetheless, Retool says that the function can also be responsible for the August breach severity because it allowed the hacker who efficiently phished an worker’s Google account to have entry to all of their 2FA codes used for inner companies.
“With these codes (and the Okta session), the attacker gained entry to our VPN, and crucially, our inner admin programs,” Kodesh stated.
“This allowed them to run an account takeover assault on a selected set of consumers (all within the crypto business). (They modified emails for customers and reset passwords.) After taking on their accounts, the attacker poked round among the Retool apps.”
As Kodesh defined, whereas, initially, Retool had enabled MFA, the auth codes synced by Google Authenticator to the cloud led to an inadvertent transition to single-factor authentication.
This shift occurred as management over the Okta account translated into management over the Google account, subsequently granting entry to all One-Time Passwords (OTPs) saved inside Google Authenticator.
“We strongly consider that Google ought to both get rid of their darkish patterns in Google Authenticator (which inspires the saving of MFA codes within the cloud), or at the least present organizations with the flexibility to disable it.”
Whereas Google Authenticator does promote its cloud sync function, it isn’t required. If in case you have enabled the function, you may disable it by clicking on the account circle on the high proper of the app and deciding on ‘Use Authenticator with out an account.’ It will log you out of the app and delete your synchronized 2FA codes in your Google account.
“Our first precedence is the security and safety of all on-line customers, whether or not shopper or enterprise, and this occasion is one other instance of why we stay devoted to enhancing our authentication applied sciences. Past this, we additionally proceed to encourage the transfer towards safer authentication applied sciences as an entire, resembling passkeys, that are phishing resistant,” a Google spokesperson instructed BleepingComputer.
Google additionally really helpful migrating to FIDO-based tech from legacy one-time password (OTP) multi-factor authentication as a easy strategy to thwart comparable assaults.
“Phishing and social engineering dangers with legacy authentication applied sciences, like ones based mostly on OTP, are why the business is closely investing in these FIDO-based applied sciences,” the Google spokesperson stated.
“Whereas we proceed to work towards these adjustments, we wish to guarantee Google Authenticator customers know they’ve a alternative whether or not to sync their OTPs to their Google Account, or to maintain them saved solely regionally. Within the meantime, we’ll proceed to work on balancing safety with usability as we contemplate future enhancements to Google Authenticator.”
No on-premise Retool clients breached
After discovering the safety incident, Retool revoked all inner worker authenticated periods, together with these for Okta and G Suite.
It additionally restricted entry to all 27 compromised accounts and notified all affected cloud clients, restoring all hijacked accounts to their unique configurations (no on-premise clients have been impacted within the incident, in accordance with Retool).
“This meant that though an attacker had entry to Retool cloud, there was nothing they might do to have an effect on on-premise clients,” Kodesh stated.
“It is value noting that the overwhelming majority of our crypto and bigger clients particularly use Retool on-premise.”
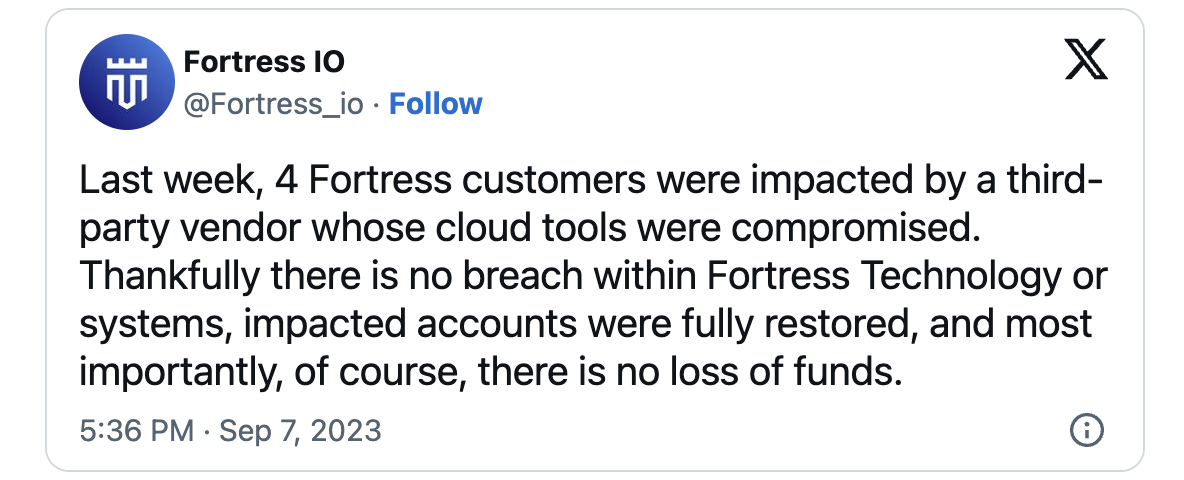
A Coindesk report linked the Retool breach to the theft of $15 million from Fortress Belief in early September.
Retool’s improvement platform is used to construct enterprise software program by corporations starting from startups to Fortune 500 enterprises, together with the likes of Amazon, Mercedes-Benz, DoorDash, NBC, Stripe, and Lyft.
Social engineering assaults focusing on IT service desks or assist personnel are more and more being utilized by risk actors to achieve preliminary entry to company networks.
The checklist of corporations that obtained hacked utilizing this tactic contains Cisco, Uber, 2K Video games, and, extra not too long ago, MGM Resorts.
In late August, Okta alerted clients of networks being breached by way of corporations’ IT service desks after hackers reset Multi-Issue Authentication (MFA) defenses for Tremendous Administrator or Org Administrator accounts.
U.S. Federal Businesses additionally warned this week of the cybersecurity dangers behind attackers utilizing deepfakes. They really helpful utilizing tech that may assist detect deepfakes used to achieve entry to their networks, communications, and delicate data following profitable social engineering assaults.
Replace: Added Google assertion.