With the widespread consideration, and potential functions of blockchain and synthetic intelligence applied sciences, the privateness safety strategies that come up as a direct results of integration of the 2 applied sciences is gaining notable significance. These privateness safety strategies not solely shield the privateness of people, however in addition they assure the dependability and safety of the info.
On this article, we will probably be speaking about how the collaboration between AI and blockchain provides delivery to quite a few privateness safety strategies, and their utility in several verticals together with de-identification, knowledge encryption, k-anonymity, and multi-tier distributed ledger strategies. Moreover, we will even attempt to analyze the deficiencies together with their precise trigger, and supply options accordingly.
The blockchain community was first launched to the world when in 2008 Nakamoto launched Bitcoin, a cryptocurrency constructed on the blockchain community. Ever since its introduction, blockchain has gained lots of reputation, particularly prior to now few years. The worth at which Bitcoin is buying and selling as we speak, and it crossing the Trillion-dollar market cap mark signifies that blockchain has the potential to generate substantial income and income for the trade.
Blockchain expertise will be categorized totally on the premise of the extent of accessibility and management they provide, with Public, Non-public, and Federated being the three fundamental forms of blockchain applied sciences. Widespread cryptocurrencies and blockchain architectures like Bitcoin and Ethereum are public blockchain choices as they’re decentralized in nature, and so they enable nodes to enter or exit the community freely, and thus promotes most decentralization.
The next determine depicts the construction of Ethereum because it makes use of a linked checklist to ascertain connections between completely different blocks. The header of the block shops the hash tackle of the previous block so as to set up a linkage between the 2 successive blocks.

The event, and implementation of the blockchain expertise is adopted with reputable safety and privateness issues in varied fields that can not be uncared for. For instance, a knowledge breach within the monetary trade may end up in heavy losses, whereas a breach in army or healthcare methods will be disastrous. To stop these situations, safety of information, consumer property, and id info has been a serious focus of the blockchain safety analysis group, as to make sure the event of the blockchain expertise, it’s important to keep up its safety.
Ethereum is a decentralized blockchain platform that upholds a shared ledger of knowledge collaboratively utilizing a number of nodes. Every node within the Ethereum community makes use of the EVM or Ethereum Vector Machine to compile good contracts, and facilitate the communication between nodes that happen by way of a P2P or peer-to-peer community. Every node on the Ethereum community is supplied with distinctive features, and permissions, though all of the nodes can be utilized for gathering transactions, and interesting in block mining. Moreover, it’s price noting that when in comparison with Bitcoin, Ethereum shows sooner block technology speeds with a lead of practically 15 seconds. It implies that crypto miners have a greater probability at buying rewards faster whereas the interval time for verifying transactions is decreased considerably.
However, AI or Synthetic Intelligence is a department in fashionable science that focuses on creating machines which might be able to decision-making, and might simulate autonomous considering similar to a human’s skill. Synthetic Intelligence is a really huge department in itself with quite a few subfields together with deep studying, pc imaginative and prescient, pure language processing, and extra. NLP specifically has been a subfield that has been focussed closely prior to now few years that has resulted within the improvement of some top-notch LLMs like GPT and BERT. NLP is headed in the direction of close to perfection, and the ultimate step of NLP is processing textual content transformations that may make computer systems comprehensible, and up to date fashions like ChatGPT constructed on GPT-4 indicated that the analysis is headed in the direction of the correct route.
One other subfield that’s fairly widespread amongst AI builders is deep studying, an AI method that works by imitating the construction of neurons. In a standard deep studying framework, the exterior enter info is processed layer by layer by coaching hierarchical community constructions, and it’s then handed on to a hidden layer for ultimate illustration. Deep studying frameworks will be categorised into two classes: Supervised studying, and Unsupervised studying.

The above picture depicts the structure of deep studying perceptron, and as it may be seen within the picture, a deep studying framework employs a multiple-level neural community structure to be taught the options within the knowledge. The neural community consists of three forms of layers together with the hidden layer, the enter payer, and the output layer. Every perceptron layer within the framework is linked to the subsequent layer so as to kind a deep studying framework.
Lastly, we have now the combination of blockchain and synthetic intelligence applied sciences as these two applied sciences are being utilized throughout completely different industries and domains with a rise within the concern relating to cybersecurity, knowledge safety, and privateness safety. Purposes that purpose to combine blockchain and synthetic intelligence manifest the combination within the following features.
- Using blockchain expertise to file and retailer the coaching knowledge, enter and output of the fashions, and parameters, guaranteeing accountability, and transparency in mannequin audits.
- Utilizing blockchain frameworks to deploy AI fashions to attain decentralization companies amongst fashions, and enhancing the scalability and stability of the system.
- Offering safe entry to exterior AI knowledge and fashions utilizing decentralized methods, and enabling blockchain networks to amass exterior info that’s dependable.
- Utilizing blockchain-based token designs and incentive mechanisms to ascertain connections and trust-worthy interactions between customers and AI mannequin builders.
Privateness Safety Via the Integration of Blockchain and AI Applied sciences
Within the present situation, knowledge belief methods have sure limitations that compromise the reliability of the info transmission. To problem these limitations, blockchain applied sciences will be deployed to ascertain a reliable and safe knowledge sharing & storage answer that gives privateness safety, and enhances knowledge safety. Among the functions of blockchain in AI privateness safety are talked about within the following desk.
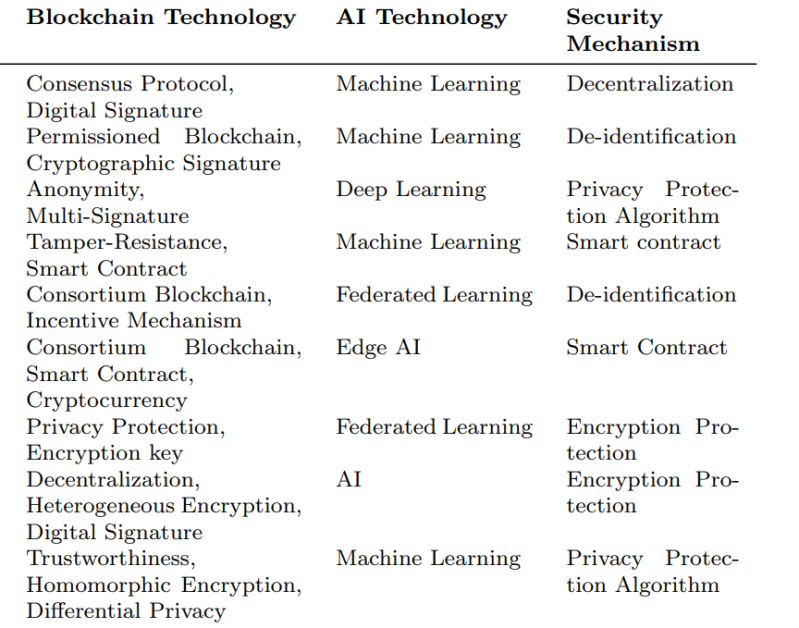
By enhancing the implementation & integration of those applied sciences, the protecting capability & safety of present knowledge belief methods will be boosted considerably.
Knowledge Encryption
Historically, knowledge sharing and knowledge storing strategies have been susceptible to safety threats as a result of they’re depending on centralized servers that makes them an simply identifiable goal for attackers. The vulnerability of those strategies provides rise to severe problems resembling knowledge tampering, and knowledge leaks, and given the present safety necessities, encryption strategies alone aren’t adequate to make sure the protection & safety of the info, which is the primary purpose behind the emergence of privateness safety applied sciences based mostly on the combination of synthetic intelligence & blockchain.
Let’s take a look at a blockchain-based privateness preserving federated studying scheme that goals to enhance the Multi-Krum method, and mix it with homomorphic encryption to attain ciphertext-level mannequin filtering and mannequin aggregation that may confirm native fashions whereas sustaining privateness safety. The Paillier homomorphic encryption method is used on this methodology to encrypt mannequin updates, and thus offering further privateness safety. The Paillier algorithm works as depicted.

De-Identification
De-Identification is a technique that’s generally used to anonymize private identification info of a consumer within the knowledge by separating the info from the info identifiers, and thus decreasing the chance of information monitoring. There exists a decentralized AI framework constructed on permissioned blockchain expertise that makes use of the above talked about method. The AI framework basically separates the private identification info from non-personal info successfully, after which shops the hash values of the private identification info within the blockchain community. The proposed AI framework will be utilized within the medical trade to share medical data & info of a affected person with out revealing his/her true id. As depicted within the following picture, the proposed AI framework makes use of two unbiased blockchain for knowledge requests with one blockchain community storing the affected person’s info together with knowledge entry permissions whereas the second blockchain community captures audit traces of any requests or queries made by requesters. Because of this, sufferers nonetheless have full authority and management over their medical data & delicate info whereas enabling safe & secure knowledge sharing inside a number of entities on the community.
Multi-Layered Distributed Ledger
A multi-layered distributed ledger is a knowledge storage system with decentralization property and a number of hierarchical layers which might be designed to maximise effectivity, and safe the info sharing course of together with enhanced privateness safety. DeepLinQ is a blockchain-based multi-layered decentralized distributed ledger that addresses a consumer’s concern relating to knowledge privateness & knowledge sharing by enabling privacy-protected knowledge privateness. DeepLinQ archives the promised knowledge privateness by using varied strategies like on-demand querying, entry management, proxy reservation, and good contracts to leverage blockchain community’s traits together with consensus mechanism, full decentralization, and anonymity to guard knowledge privateness.
Okay-Anonymity
The Okay-Anonymity methodology is a privateness safety methodology that goals to focus on & group people in a dataset in a method that each group has a minimum of Okay people with an identical attribute values, and due to this fact defending the id & privateness of particular person customers. The Okay-Anonymity methodology has been the premise of a proposed dependable transactional mannequin that facilitates transactions between vitality nodes, and electrical autos. On this mannequin, the Okay-Anonymity methodology serves two features: first, it hides the situation of the EVs by developing a unified request utilizing Okay-Anonymity strategies that conceal or cover the situation of the proprietor of the automotive; second, the Okay-Anonymity methodology conceals consumer identifiers in order that attackers aren’t left with the choice to hyperlink customers to their electrical autos.
Analysis and State of affairs Evaluation
On this part, we will probably be speaking about complete evaluation and analysis of ten privateness safety methods utilizing the fusion of blockchain and AI applied sciences which were proposed in recent times. The analysis focuses on 5 main traits of those proposed strategies together with: authority administration, knowledge safety, entry management, scalability and community safety, and in addition discusses the strengths, weaknesses, and potential areas of enchancment. It is the distinctive options ensuing from the combination of AI and blockchain applied sciences which have paved methods for brand spanking new concepts, and options for enhanced privateness safety. For reference, the picture beneath exhibits completely different analysis metrics employed to derive the analytical outcomes for the mixed utility of the blockchain and AI applied sciences.

Authority Administration
Entry management is a safety & privateness expertise that’s used to limit a consumer’s entry to licensed sources on the premise of pre-defined guidelines, set of directions, insurance policies, safeguarding knowledge integrity, and system safety. There exists an clever privateness parking administration system that makes use of a Position-Primarily based Entry Management or RBAC mannequin to handle permissions. Within the framework, every consumer is assigned a number of roles, and are then categorised in response to roles that permits the system to regulate attribute entry permissions. Customers on the community could make use of their blockchain tackle to confirm their id, and get attribute authorization entry.
Entry Management
Entry management is likely one of the key fundamentals of privateness safety, proscribing entry based mostly on group membership & consumer id to make sure that it’s only the licensed customers who can entry particular sources that they’re allowed to entry, and thus defending the system from undesirable to pressured entry. To make sure efficient and environment friendly entry management, the framework wants to think about a number of components together with authorization, consumer authentication, and entry insurance policies.
Digital Id Know-how is an rising method for IoT functions that may present secure & safe entry management, and guarantee knowledge & machine privateness. The strategy proposes to make use of a sequence of entry management insurance policies which might be based mostly on cryptographic primitives, and digital id expertise or DIT to guard the safety of communications between entities resembling drones, cloud servers, and Floor Station Servers (GSS). As soon as the registration of the entity is accomplished, credentials are saved within the reminiscence. The desk included beneath summarizes the forms of defects within the framework.

Knowledge Safety
Knowledge safety is used to discuss with measures together with knowledge encryption, entry management, safety auditing, and knowledge backup to make sure that the info of a consumer isn’t accessed illegally, tampered with, or leaked. In relation to knowledge processing, applied sciences like knowledge masking, anonymization, knowledge isolation, and knowledge encryption can be utilized to guard knowledge from unauthorized entry, and leakage. Moreover, encryption applied sciences resembling homomorphic encryption, differential privateness safety, digital signature algorithms, uneven encryption algorithms, and hash algorithms, can forestall unauthorized & unlawful entry by non-authorized customers and guarantee knowledge confidentiality.
Community Safety
Community safety is a broad discipline that encompasses completely different features together with guaranteeing knowledge confidentiality & integrity, stopping community assaults, and defending the system from community viruses & malicious software program. To make sure the protection, reliability, and safety of the system, a sequence of safe community architectures and protocols, and safety measures should be adopted. Moreover, analyzing and assessing varied community threats and arising with corresponding protection mechanisms and safety methods are important to enhance the reliability & safety of the system.

Scalability
Scalability refers to a system’s skill to deal with bigger quantities of information or an growing variety of customers. When designing a scalable system, builders should think about system efficiency, knowledge storage, node administration, transmission, and several other different components. Moreover, when guaranteeing the scalability of a framework or a system, builders should bear in mind the system safety to stop knowledge breaches, knowledge leaks, and different safety dangers.
Builders have designed a system in compliance with European Common Knowledge Safety Guidelines or GDPR by storing privacy-related info, and paintings metadata in a distributed file system that exists off the chain. Paintings metadata and digital tokens are saved in OrbitDB, a database storage system that makes use of a number of nodes to retailer the info, and thus ensures knowledge safety & privateness. The off-chain distributed system disperses knowledge storage, and thus improves the scalability of the system.

State of affairs Evaluation
The amalgamation of AI and blockchain applied sciences has resulted in creating a system that focuses closely on defending the privateness, id, and knowledge of the customers. Though AI knowledge privateness methods nonetheless face some challenges like community safety, knowledge safety, scalability, and entry management, it’s essential to think about and weigh these points on the premise of sensible concerns in the course of the design section comprehensively. Because the expertise develops and progresses additional, the functions broaden, the privateness safety methods constructed utilizing AI & blockchain will draw extra consideration within the upcoming future. On the premise of analysis findings, technical approaches, and utility situations, they are often categorised into three classes.
- Privateness safety methodology utility within the IoT or Web of Issues trade by using each blockchain and AI expertise.
- Privateness safety methodology utility in good contract and companies that make use of each blockchain and AI expertise.
- Giant-scale knowledge evaluation strategies that supply privateness safety by using each blockchain and AI expertise.
The applied sciences belonging to the primary class give attention to the implementation of AI and blockchain applied sciences for privateness safety within the IoT trade. These strategies use AI strategies to investigate excessive volumes of information whereas benefiting from decentralized & immutable options of the blockchain community to make sure authenticity and safety of the info.
The applied sciences falling within the second class give attention to fusing AI & Blockchain applied sciences for enhanced privateness safety by making use of blockchain’s good contract & companies. These strategies mix knowledge evaluation and knowledge processing with AI and use blockchain expertise alongside to scale back dependency on trusted third events, and file transactions.
Lastly, the applied sciences falling within the third class give attention to harnessing the ability of AI and blockchain expertise to attain enhanced privateness safety in large-scale knowledge analytics. These strategies purpose to use blockchain’s decentralization, and immutability properties that make sure the authenticity & safety of information whereas AI strategies make sure the accuracy of information evaluation.
Conclusion
On this article, we have now talked about how AI and Blockchain applied sciences can be utilized in sync with one another to boost the functions of privateness safety applied sciences by speaking about their associated methodologies, and evaluating the 5 major traits of those privateness safety applied sciences. Moreover, we have now additionally talked concerning the current limitations of the present methods. There are specific challenges within the discipline of privateness safety applied sciences constructed upon blockchain and AI that also should be addressed like how you can strike a steadiness between knowledge sharing, and privateness preservation. The analysis on how you can successfully merge the capabilities of AI and Blockchain strategies is occurring, and listed here are a number of different ways in which can be utilized to combine different strategies.
Edge computing goals to attain decentralization by leveraging the ability of edge & IoT units to course of personal & delicate consumer knowledge. As a result of AI processing makes it necessary to make use of substantial computing sources, utilizing edge computing strategies can allow the distribution of computational duties to edge units for processing as an alternative of migrating the info to cloud companies, or knowledge servers. For the reason that knowledge is processed a lot nearer the sting machine itself, the latency time is decreased considerably, and so is the community congestion that enhances the pace & efficiency of the system.
Multi-chain mechanisms have the potential to resolve single-chain blockchain storage, and efficiency points, due to this fact boosting the scalability of the system. The combination of multi-chain mechanisms facilitates distinct attributes & privacy-levels based mostly knowledge classification, due to this fact bettering storage capabilities and safety of privateness safety methods.

