
Safety researchers noticed a brand new marketing campaign they attribute to the Charming Kitten APT group the place hackers used new NokNok malware that targets macOS programs.
The marketing campaign began in Might and depends on a distinct an infection chain than beforehand noticed, with LNK information deploying the payloads as an alternative of the standard malicious Phrase paperwork seen in previous assaults from the group.
Charming Kitten is also referred to as APT42 or Phosphorus and has launched no less than 30 operations in 14 nations since 2015, in response to in response to Mandiant.
Google has linked the risk actor to the Iranian state, extra particularly, the Islamic Revolutionary Guard Corps (IRGC).
In September 2022, the U.S. authorities managed to establish and cost members of the risk group.
Proofpoint reviews that the risk actor has now deserted the macro-based an infection strategies involving laced Phrase paperwork and as an alternative deploys LNK information to load their payloads.
Relating to the phishing lures and social engineering strategies seen within the marketing campaign, the hackers posed as nuclear consultants from the U.S. and approached targets with a suggestion to evaluation drafts on international coverage matters.
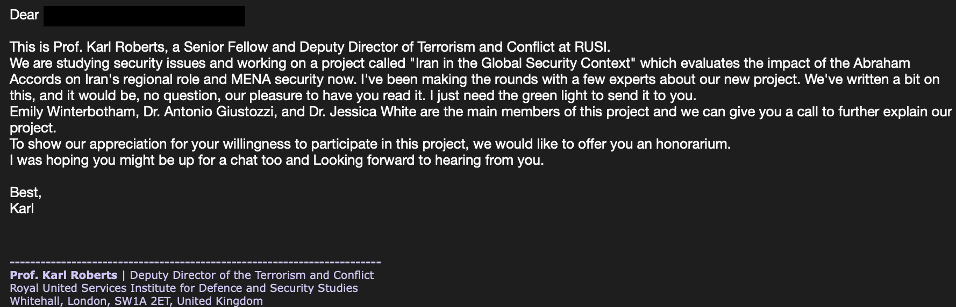
In lots of circumstances, the attackers insert different personas within the dialog so as to add a way of legitimacy and set up a rapport with the goal.
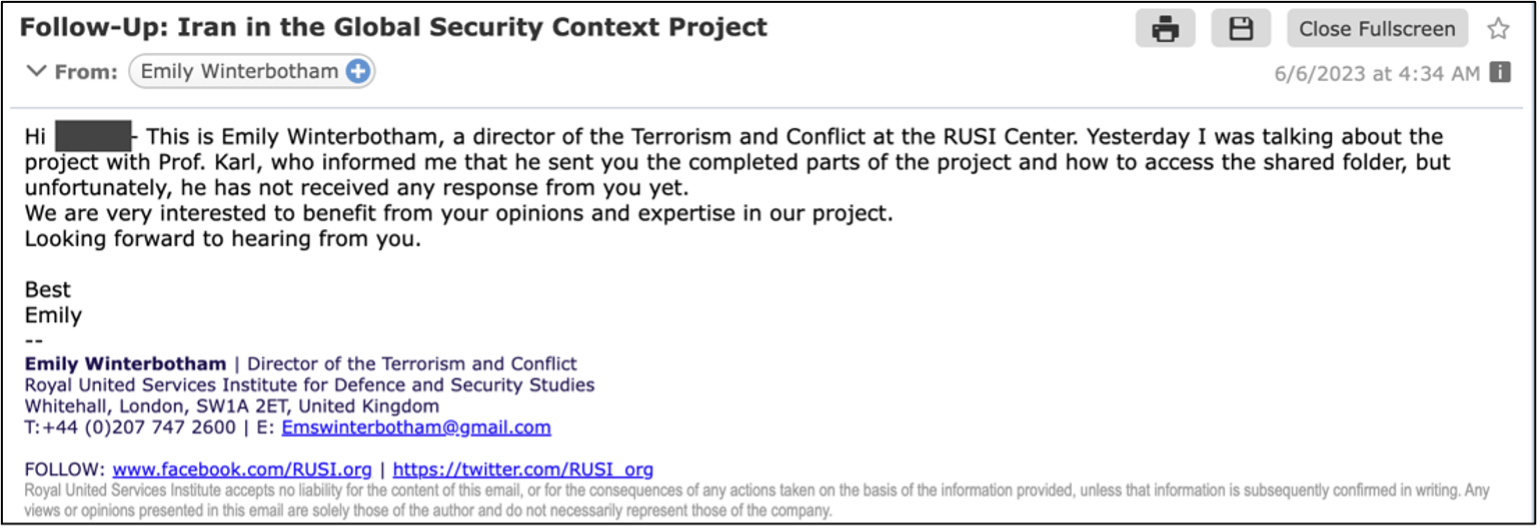
Charming Kitten’s impersonation or faux persona assumption in phishing assaults has been documented, and so has its use of ‘sock puppets’ to create real looking dialog threads.
Assaults on Home windows
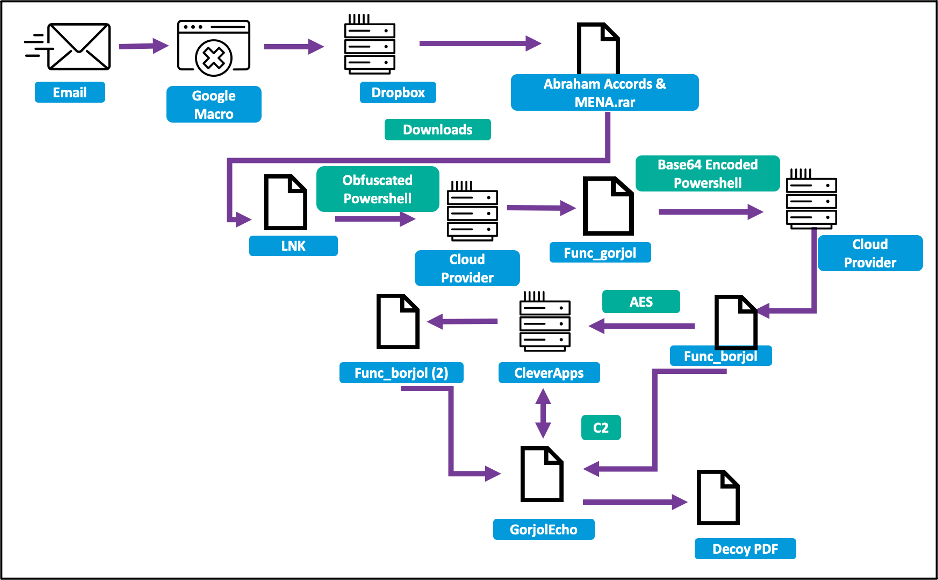
After gaining the goal’s belief, Charming Kitten sends a malicious hyperlink that incorporates a Google Script macro, redirecting the sufferer to a Dropbox URL.
This exterior supply hosts a password-protected RAR archive with a malware dropper that leverages PowerShell code and an LNK file to stage the malware from a cloud internet hosting supplier.
The ultimate payload is GorjolEcho, a easy backdoor that accepts and executes instructions from its distant operators.
To keep away from elevating suspicion, GorjolEcho will open a PDF with a subject related to the dialogue the attackers had with the goal beforehand.
Assaults on macOS
If the sufferer makes use of macOS, which the hackers usually understand after they fail to contaminate them with the Home windows payload, they ship a brand new hyperlink to “library-store[.]camdvr[.]org” that hosts a ZIP file masquerading as a RUSI (Royal United Companies Institute) VPN app.
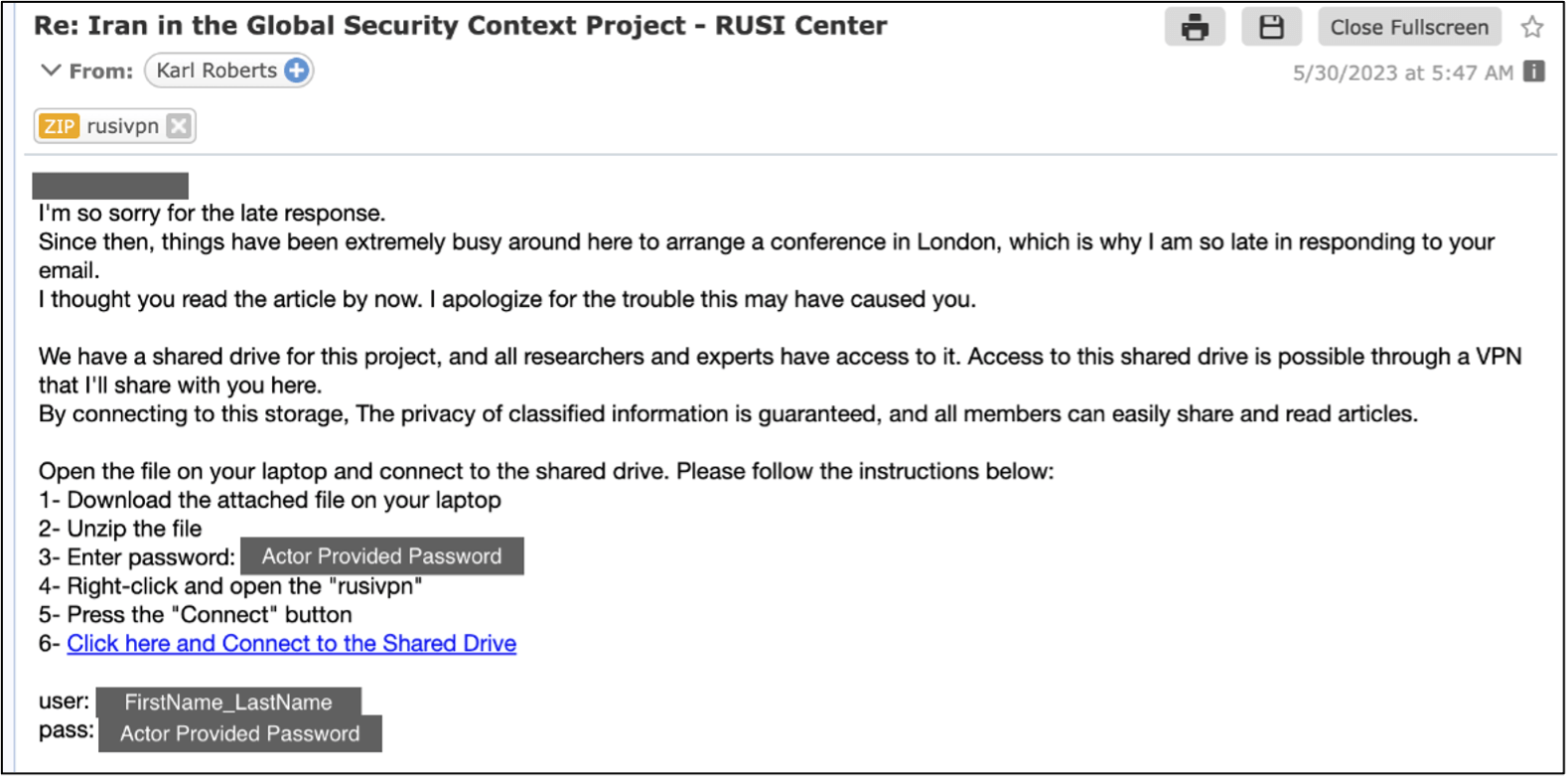
When executing the Apple script file within the archive, a curl command fetches the NokNok payload and establishes a backdoor onto the sufferer’s system.
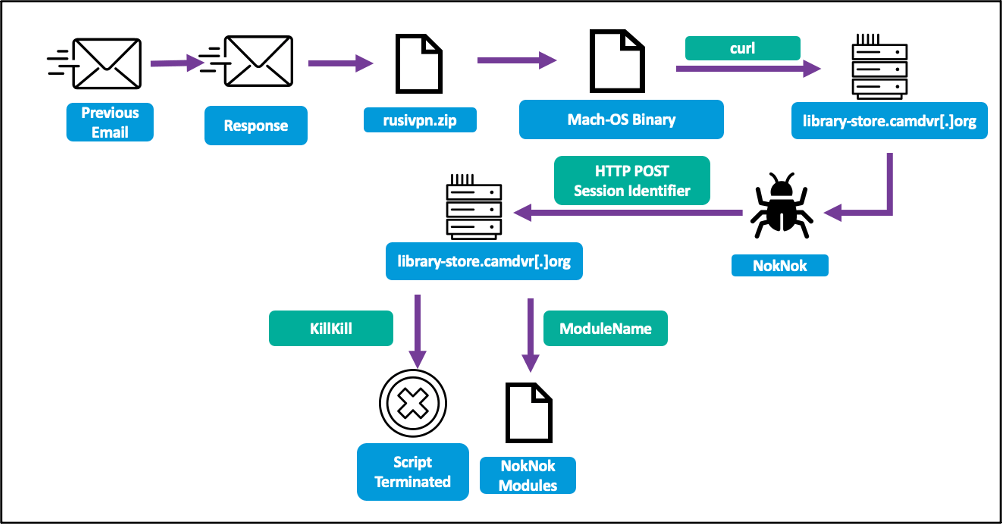
NokNok generates a system identifier after which makes use of 4 bash script modules to set persistence, set up communication with the command and management (C2) server, after which begins exfiltrating knowledge to it.
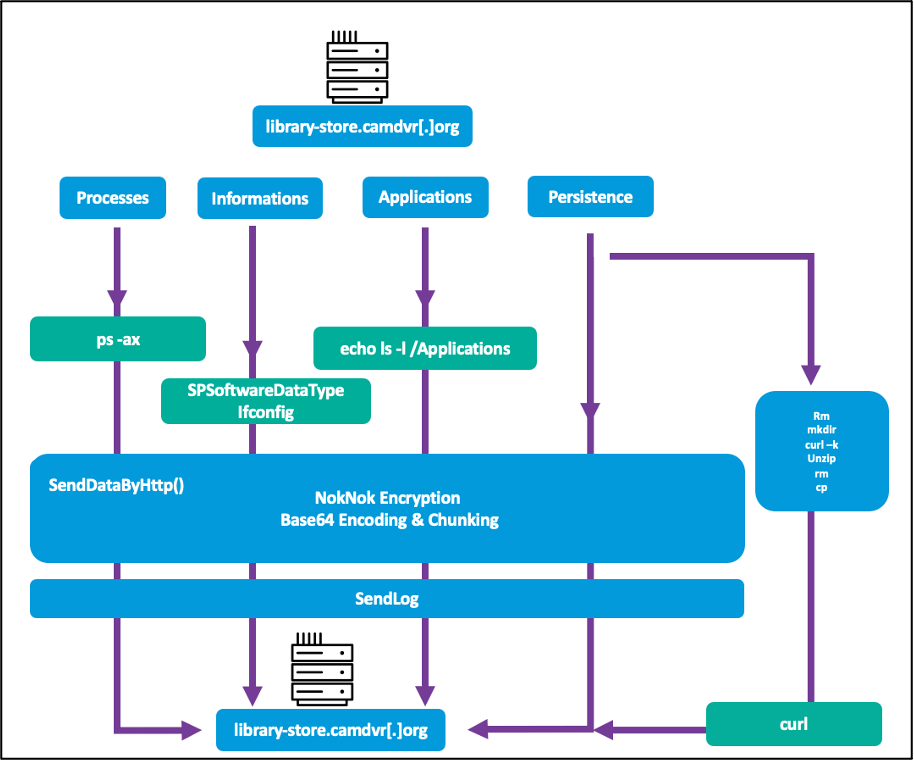
The NokNok malware gathers system info that features the model of the OS, working processes, and put in functions.
NokNok encrypts all collected knowledge, encodes it within the base64 format, and exfiltrates it.
Proofpoint additionally mentions that NokNok would possibly characteristic extra particular espionage-related performance by different unseen modules.
The suspicion is primarily based on code similarities to GhostEcho, beforehand analyzed by Verify Level.
That backdoor featured modules that allowed taking screenshots, command execution, and cleansing the an infection path. It’s seemingly that NokNok has these features too.
Total, this marketing campaign reveals that Charming Kitten has a excessive diploma of adaptability, is able to focusing on macOS programs when needed, and highlights the rising risk of refined malware campaigns to macOS customers.
