
Microsoft says a North Korean hacking group has breached Taiwanese multimedia software program firm CyberLink and trojanized certainly one of its installers to push malware in a provide chain assault focusing on potential victims worldwide.
In response to Microsoft Risk Intelligence, exercise suspected to be linked with the altered CyberLink installer file surfaced as early as October 20, 2023.
This trojanized installer has been detected on greater than 100 gadgets throughout numerous nations worldwide, together with Japan, Taiwan, Canada, and america.
Microsoft safety specialists have attributed this provide chain assault with excessive confidence to a North Korean cyberespionage group tracked by Redmond as Diamond Sleet (aka ZINC, Labyrinth Chollima, and Lazarus).
The second-stage payload noticed whereas investigating this assault interacts with infrastructure that the identical group of menace actors beforehand compromised.
“Diamond Sleet utilized a reliable code signing certificates issued to CyberLink Corp. to signal the malicious executable,” the corporate stated.
“This certificates has been added to Microsoft’s disallowed certificates listing to guard clients from future malicious use of the certificates.”
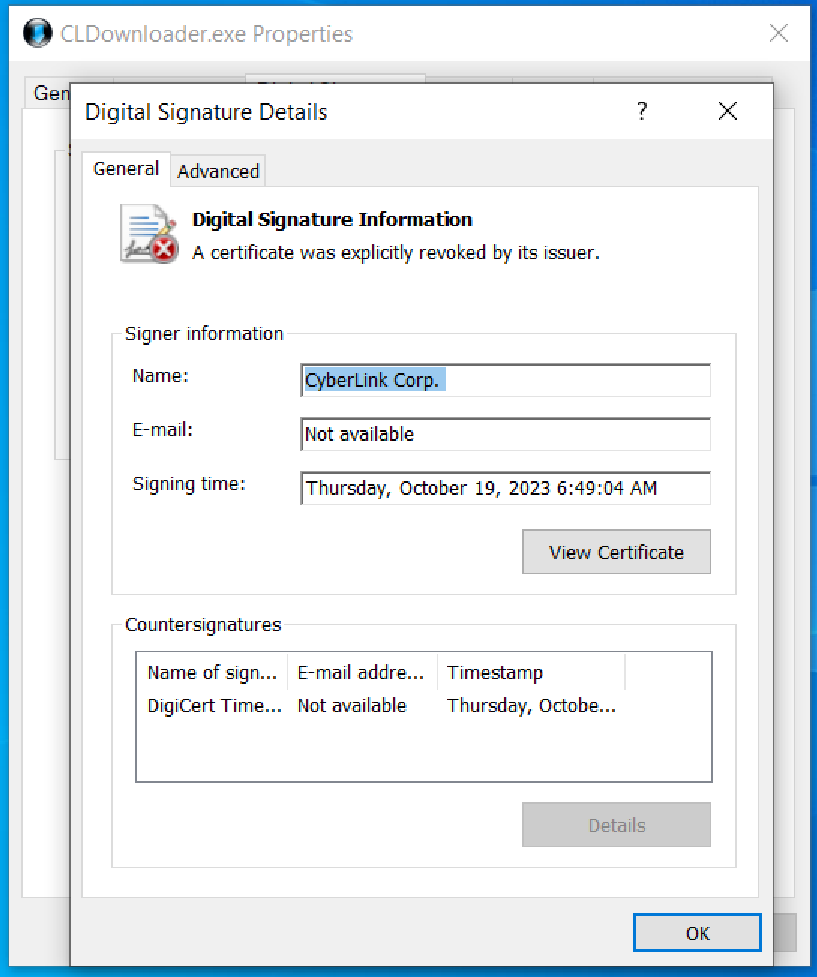
Microsoft tracks the trojanized software program and associated payloads as LambLoad, a malware downloader and loader.
LambLoad targets methods not protected by FireEye, CrowdStrike, or Tanium safety software program. If these circumstances are unmet, the malicious executable continues operating with out executing the bundled malicious code.
Nonetheless, if the factors are met, the malware connects with certainly one of three command-and-control (C2) servers to retrieve a second-stage payload hid inside a file posing as a PNG file utilizing the static Consumer-Agent ‘Microsoft Web Explorer.’
“The PNG file comprises an embedded payload inside a pretend outer PNG header that’s, carved, decrypted, and launched in reminiscence,” Microsoft says.
It is a widespread assault methodology utilized by the Lazarus North Korean menace actors, who’re recognized for trojanizing reliable cryptocurrency software program to steal crypto property.
Despite the fact that Microsoft has but to detect hands-on-keyboard exercise following LambLoad malware breaches, the Lazarus hackers are recognized for:
- Stealing delicate information from compromised methods
- Infiltrating software program construct environments
- Progressing downstream to use additional victims
- Establishing persistent entry to victims’ environments
After detecting a provide chain assault, Microsoft knowledgeable CyberLink and can be notifying Microsoft Defender for Endpoint clients who have been affected by the assault.
Microsoft additionally reported the assault to GitHub, which eliminated the second-stage payload as per its Acceptable Use Insurance policies.
A CyberLink spokesperson didn’t instantly reply to BleepingComputer’s request for remark.
Who’s Lazarus?
The Lazarus Group is a North Korean-sponsored hacking group that has been working for greater than ten years, since at the least 2009.
Recognized for focusing on organizations worldwide, their operations have to this point included assaults on monetary establishments, media shops, and authorities companies.
Lazarus has been linked to a large vary of malicious actions encompassing espionage, information breaches, and monetary exploitation. Their campaigns additionally concerned focusing on safety researchers, embedding malicious code in open-source cryptocurrency platforms, executing huge cryptocurrency heists, and utilizing sham job interviews to disseminate malware.
The group is considered behind many high-profile cyber assaults, together with the 2014 Sony Photos hack, the WannaCry ransomware assault of 2017, and the most important crypto hack ever in 2022.
