A brand new Mirai-based malware botnet named ‘InfectedSlurs’ has been exploiting two zero-day distant code execution (RCE) vulnerabilities to contaminate routers and video recorder (NVR) gadgets.
The malware hijacks the gadgets to make them a part of its DDoS (distributed denial of service) swarm, presumably rented for revenue.
The invention of ‘InfectedSlurs’ comes from Akamai, who first noticed it on its honeypots in late October 2023. Nonetheless, the botnet’s preliminary exercise dates again to late 2022.
The cybersecurity firm reviews that the impacted distributors have not patched the 2 exploited flaws but; therefore, particulars about them have been reserved for now.
Discovery and targets
Akamai’s Safety Intelligence Response Crew (SIRT) first found the botnet in October 2023, noticing uncommon exercise on a not often used TCP port concentrating on their honeypots.
The exercise involved low-frequency probes making an attempt authentication through POST requests, adopted by a command injection try.
Based mostly on the info they held, SIRT analysts performed an internet-wide scan and found that the focused gadgets have been linked to a selected NVR producer, not named within the report for safety causes.
The botnet leverages an undocumented RCE flaw to realize unauthorized entry to the gadget.
“The SIRT did a fast test for CVEs identified to affect this vendor’s NVR gadgets and was stunned to search out that we have been taking a look at a brand new zero-day exploit being actively leveraged within the wild,” reads Akamai’s report.
“By means of the accountable disclosure course of, the seller communicated to us they’re engaged on a repair that may probably be deployed in December 2023.”
Additional examination confirmed that the malware additionally makes use of default credentials documented within the vendor’s manuals for a number of NVR merchandise to put in a bot consumer and carry out different malicious actions.
Trying nearer into the marketing campaign, Akamai found that the botnet additionally targets a wi-fi LAN router common amongst dwelling customers and inns, which suffers from one other zero-day RCE flaw leveraged by the malware.
The unnamed vendor of the router gadget promised to launch safety updates that tackle the issue in December 2023.
InfectedSlurs particulars
‘InfectedSlurs,’ named like that attributable to the usage of offensive language within the C2 (command and management) domains and hardcoded strings, is a JenX Mirai variant.
Akamai reviews that its C2 infrastructure is comparatively concentrated and likewise seems to assist hailBot operations.
Evaluation revealed a now-deleted Telegram account linked to the cluster on Telegram.
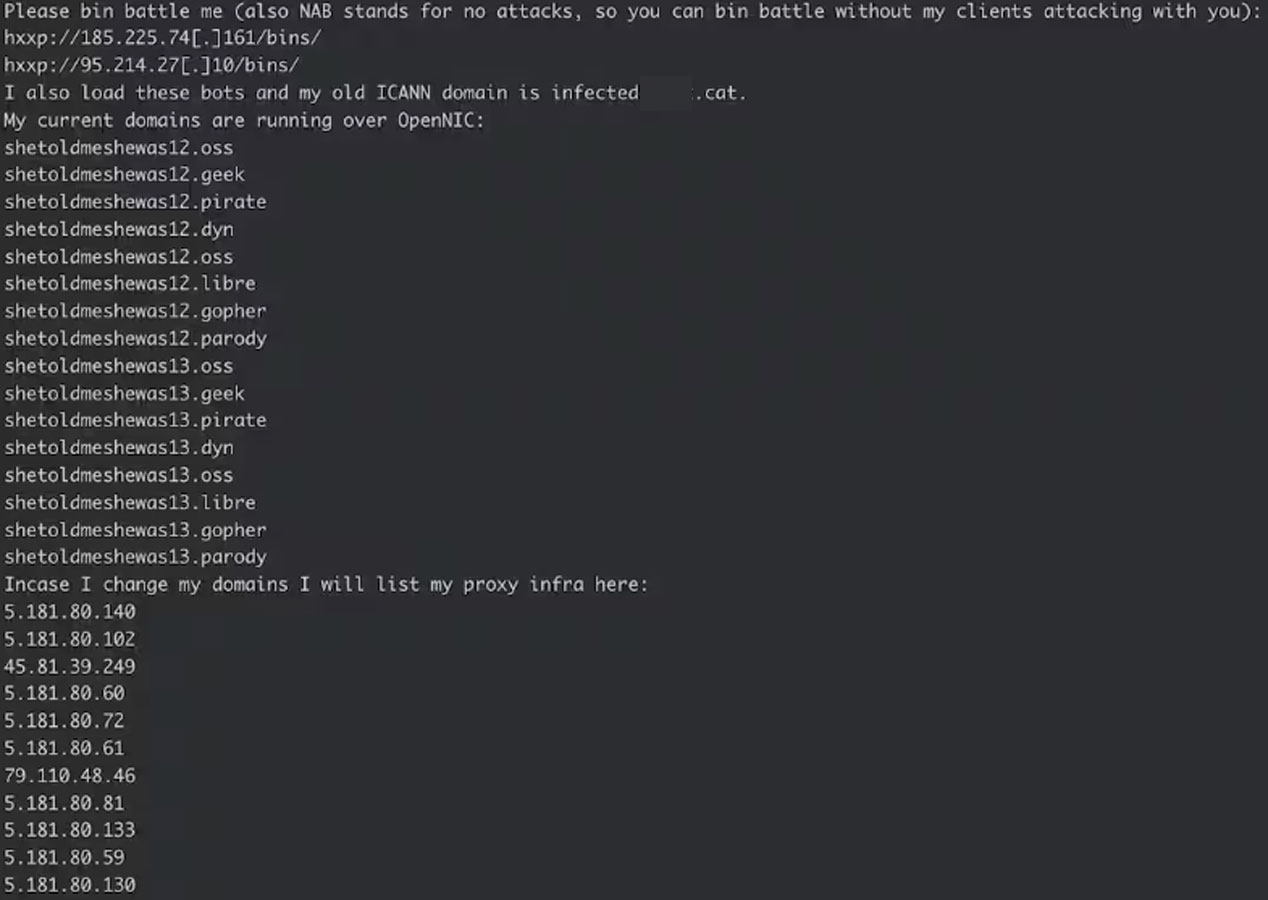
The person additionally posted screenshots exhibiting almost ten thousand bots within the Telnet protocol and one other 12,000 on particular gadget sorts/manufacturers known as “Vacron,” “ntel,” and “UTT-Bots.”
Akamai says that evaluation of the bot samples it caught in October 2023 exhibits little code modifications in comparison with the unique Mirai botnet, so it is a self-propagating DDoS instrument supporting assaults utilizing SYN, UDP, and HTTP GET request floods.
Like Mirai, InfectedSlurs does not embrace a persistence mechanism. Given the shortage of a patch for the affected gadgets, rebooting your NVR and rooter gadgets ought to briefly disrupt the botnet.
