
Hacktivist teams that function for political or ideological motives make use of a broad vary of funding strategies to assist their operations.
Israeli cyber-intelligence agency KELA notes that though hacktivism seems to be about inflicting service disruption by DDoS assaults or fame harm through information leaks, the modus operandi of those menace teams encompasses a broader scope of actions, together with frequent cybercrime ways.
These ways embrace stealing and promoting information, promoting malware and botnet licenses, demanding ransom from victims, and even providing hack-for-hire providers geared toward targets with no political significance.
Going past donations
Beginning with the pro-Russia group Killnet, KELA says the hacktivists promoted a botnet for rent in November 2021, however their monetization strategies expanded considerably in 2023.
Killnet arrange a hack-for-hire service in March 2023, introduced a brand new DDoS-for-hire service in July 2023, and launched a ‘Darkish College’ coaching program promoting 9 hacking programs to hackers in Could 2023.
Additionally in Could, because the group’s following grew on Telegram, Killnet introduced a cryptocurrency trade platform that charged a service fee between 3-4%.
Between November 2022 and April 2023, Killnet was noticed trying to promote logs, information, and entry to networks on their Telegram channels and the Infinity discussion board, which is owned and operated by the group and likewise options commercials.
Lastly, Killnet has tried to extort victims into paying ransom to cease DDoS assaults or delete stolen information, like within the case of RuTor in August 2022, BlackSprut in November 2022, the Latvian authorities in November 2022, and NATO in April 2023.
Nameless Russia, one other pro-Kremlin hacktivist group, has additionally displayed monetization actions past politically-motivated DDoS assaults focusing on European international locations.
In April 2023, the group switched from requesting donations to launching paid providers just like the Tesla botnet malware marketed on the group’s Telegram channel.
In Could 2023, Nameless Russia introduced the launch of a brand new DDoS service to focus on Tor websites, clearly aiming at shoppers from the darkish internet area.
Subsequent is Phoenix, additionally a pro-Russian DDoS group that originally launched as a sub-team of Legion and which shortly adopted different monetization strategies like promoting stolen information on Telegram beginning in March 2023.
Claimed victims of Phoenix who had been brazenly extorted on the group’s Telegram channel embrace the regulation agency Michele Bonetti and the telecom agency Mobile Pacific.
The group’s chief has additionally said that they privately provide DDoS-for-hire providers, whereas he delivers private hacker coaching programs through Telegram for a charge of as much as $2,675.
In April 2023, Phoenix introduced they might start video and audio streaming their assaults, permitting the best bidder entry to the reside stream.
Nameless Sudan, a hacktivist group that emerged in January 2023 and has documented ties with Killnet, additionally sells stolen information on their Telegram channel, in keeping with KELA.
In March 2023, the group tried to promote what they claimed to be information stolen from Air France for $3,000, whereas they demanded a cost of $3,500 from Scandinavian Airways (SAS) to cease the assaults.
In June 2023, Nameless Sudan introduced that they had attacked Microsoft and demanded a cost of $1,000,000 to cease the DDoS assaults that crippled the agency’s providers.
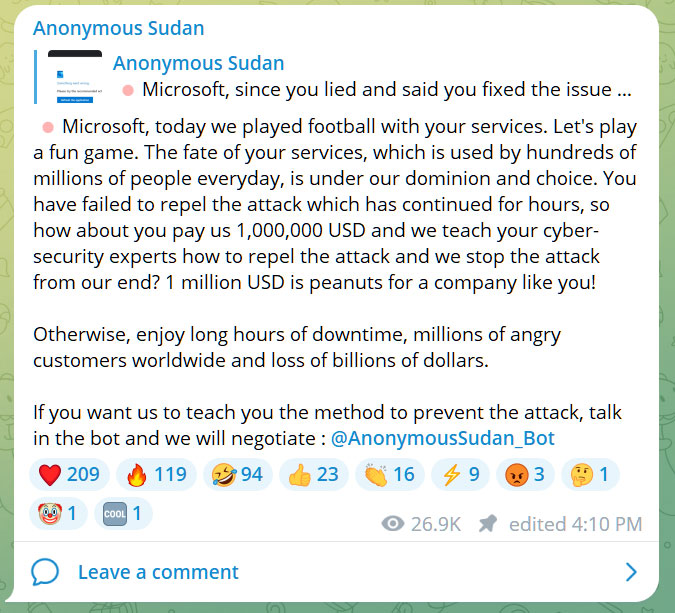
Supply: BleepingComputer
In July 2023, they marketed the sale of a database supposedly containing the information of 30 million Microsoft accounts for $50,000.
Arvin Membership is a hacktivist group preventing towards the Iranian regime by launching DDoS assaults towards authorities ministries and organizations, energetic since 2019.
In April 2023, the group launched a non-public subscription-based ($49) Telegram channel to promote information stolen from their assaults, latest exploits and vulnerabilities, and extra.
Lastly, KELA’s report highlights the pro-Russian hacktivist group Ardour, which emerged in December 2022 utilizing its personal botnet to assault Ukrainian organizations.
Mere days after the group’s launch that botnet was provided on the market beginning at $30/week, whereas the most recent model that can be out there for buy was introduced in March 2023.
To not be handled calmly
KELA believes these hacktivist teams are monetizing their operations primarily to remain energetic and proceed launching highly effective assaults at their goal. Nonetheless, no matter their funding, it doesn’t make them much less harmful to web customers and organizations.
For instance, in early June, Microsoft suffered a number of outages towards the net portal for Azure, Microsoft OneDrive, and Microsoft Outlook.
Whereas Nameless Sudan claimed credit score for the assaults throughout this era, it wasn’t till ten days later that Microsoft lastly admitted that their providers had been disrupted in DDoS assaults, illustrating the damaging potential behind hacktivists teams.
The implications of knowledge theft and the publicity of delicate data stay vital no matter whether or not they’re main or secondary aims.
Whereas some researchers think about these hacktivist teams low-level menace actors as a consequence of their harm potential and enterprise disruption, it could be wiser to contemplate them in the identical mild as common cybercriminals.
