
The FBI is warning of a brand new tactic utilized by cybercriminals the place they promote malicious “beta” variations of cryptocurrency funding apps on well-liked cell app shops which might be then used to steal crypto.
The menace actors submit the malicious apps to the cell app shops as “betas,” that means that they’re in an early improvement part and are meant for use by tech fans or followers to check and submit suggestions to builders earlier than the software program is formally launched.
The good thing about this method is that beta apps don’t undergo a regular, rigorous code evaluation course of however are as a substitute superficially scrutinized for his or her security.
This much less thorough code evaluation course of is inadequate to uncover the hidden malicious code that prompts post-installation to carry out numerous hostile actions.
“The malicious apps allow theft of personally identifiable info (PII), monetary account entry, or gadget takeover,” explains the FBI.
“The apps might seem professional by utilizing names, pictures, or descriptions much like well-liked apps.”
Often, the apps mimic cryptocurrency funding and digital asset administration instruments, asking the person to enter their professional account particulars, deposit cash for investments, and so forth.
Victims are directed to those apps by way of social engineering utilizing phishing or romance scams, they usually look professional as they’re hosted on respected app shops.
Sophos first documented this drawback in March 2022 in a report that warned about scammers abusing Apple’s TestFlight system, a platform created to assist builders distribute beta apps for testing in iOS.
A extra current Sophos report explores a malicious app marketing campaign known as ‘CryptoRom’, which masquerades as cryptocurrency funding rip-off apps. These apps are promoted by the Apple TestFlight system, which the menace actors proceed to abuse for malware distribution.
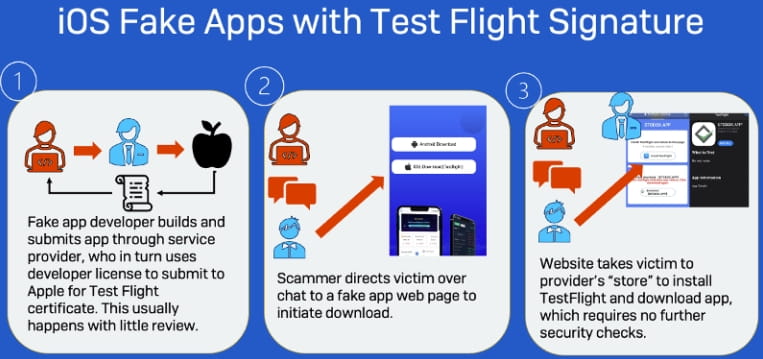
The menace actors initially add what seems to be a professional app to the iOS app retailer to be used on Take a look at Flight.
Nonetheless, after the app is accredited, the menace actors change the URL utilized by the app to level to a malicious server, introducing the malicious habits into the app.
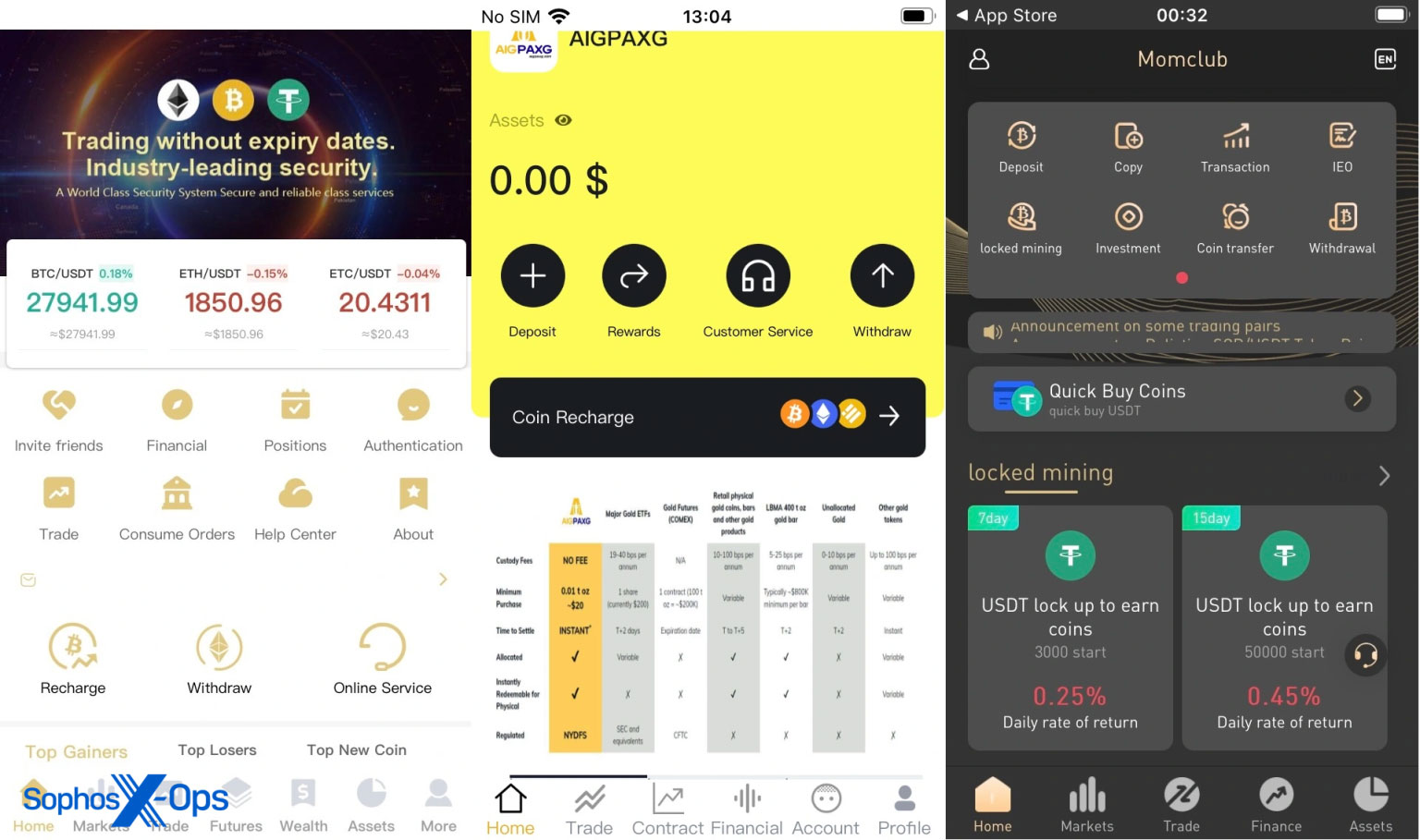
Supply: Sophos
Google’s Play retailer additionally helps the submission of beta testing apps; nonetheless, it’s unclear if extra lenient code evaluation processes are adopted there too.
FBI suggested that you just all the time verify whether or not an app’s writer is respected by studying person evaluations on the app retailer and avoiding software program with only a few downloads or excessive obtain counts mixed with only a few or no person evaluations.
Customers also needs to be cautious through the set up part of a brand new app and look at the requested permissions for something that seems to be unrelated to that software program’s core performance.
Some widespread indicators of malware in your gadget embody unusually excessive battery drain fee, elevated web knowledge consumption, sudden look of pop-up adverts, efficiency degradation, and overheating.
Replace 8/15 – A Google spokesperson has informed BleepingComputer that apps which might be in open beta testing and are publicly out there on Google Play undergo the identical evaluation course of as apps which might be in manufacturing, so there isn’t any distinction there.
