
Two stack-based buffer overflows collectively tracked as CVE-2023-32560 affect Ivanti Avalanche, an enterprise mobility administration (EMM) resolution designed to handle, monitor, and safe a variety of cellular units.
The failings are rated vital (CVSS v3: 9.8) and are remotely exploitable with out consumer authentication, probably permitting attackers to execute arbitrary code on the goal system.
The vulnerability impacts WLAvalancheService.exe model 6.4.0.0 and older, which receives communications over TCP port 1777.
An attacker sending specifically crafted information packets containing hex strings (kind 3) or an inventory of decimal strings separated by “;” (kind 9) could cause a buffer overflow on account of a fixed-size stack-based buffer used to retailer the transformed information.
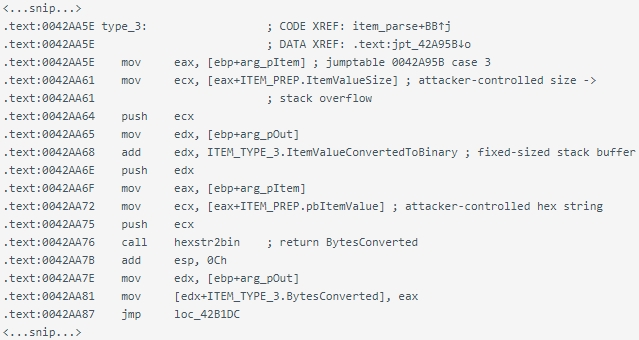
Buffer overflow is a kind of safety downside the place a program writes extra information to an adjoining reminiscence block (buffer) than it could actually maintain, overwriting these areas and inflicting program crashes or arbitrary code execution.
Stack-based buffer overflows concern the overwrite of areas allotted on the stack, a reminiscence area that shops this system’s native variables and return addresses, making it attainable to direct this system to execute malicious code.
The problems have been found by Tenable researchers and reported to Ivanti on April 4, 2023, whereas a proof-of-concept was shared with the seller on April 13, 2023.
After extending the disclosure window to permit the seller extra time to handle the problems, a safety replace was launched on August 3, 2023, with Avalanche model 6.4.1.
Together with CVE-2023-32560, Avalanche model 6.4.1 additionally fixes CVE-2023-32561, CVE-2023-32562, CVE-2023-32563, CVE-2023-32564, CVE-2023-32565, and CVE-2023-32566, regarding numerous authentication bypass and distant code execution flaws.
Ivanti software program is utilized in vital methods and settings, so menace actors are consistently in search of critical-severity vulnerabilities that represent potential gateways for assaults.
Final month, it was revealed that hackers exploited a zero-day authentication bypass vulnerability (CVE-2023-35078) in Ivanti Endpoint Supervisor Cell (EPMM) to breach a platform utilized by twelve ministries of the Norwegian authorities, accessing probably delicate and labeled info.
