
Serde, a well-liked Rust (de)serialization challenge, has determined to ship its serde_derive macro as a precompiled binary.
The transfer has generated a good quantity of push again amongst builders who fear about its future authorized and technical implications, together with a possible for provide chain assaults, ought to the maintainer account publishing these binaries be compromised.
In accordance with the Rust package deal registry, crates.io, serde has been downloaded over 196 million occasions over its lifetime, whereas the serde_derive macro has scored greater than 171 million downloads, testifying to the challenge’s widespread circulation.
Serde macro goes precompiled: there isn’t any strategy to opt-out
About three weeks in the past, a Rust programmer utilizing the Serde challenge of their utility seen one thing odd.
“I am engaged on packaging serde for Fedora Linux, and I seen that latest variations of serde_derive ship a precompiled binary now,” wrote Fabio Valentini, a Fedora Packaging Committee member.
“That is problematic for us, since we can not, certainly not (with solely only a few exceptions, for firmware or the like), redistribute precompiled binaries.”
Serde is a generally used serialization and deserialization framework for Rust knowledge buildings that, in response to its web site, is designed to conduct these operations “effectively and generically.”
“The Serde ecosystem consists of information buildings that know find out how to serialize and deserialize themselves together with knowledge codecs that know find out how to serialize and deserialize different issues,” states the challenge’s web site. Whereas, “derive” is one in every of its macros.
Valentini additional inquired to the challenge maintainers, how have been these new binaries “truly produced,” and if it will be attainable for him to recreate the binaries, versus consuming precompiled variations.
David Tolnay, who’s the first Serde maintainer, responded with potential workarounds on the time. However, that is to not say that everybody is happy.
Following an inflow of feedback from builders as to why the choice wasn’t greatest fitted to the challenge, Tolnay acknowledged the suggestions, previous to closing the GitHub concern.
His justification for delivery precompiled binaries is reproduced in entire beneath.
“The precompiled implementation is the one supported approach to make use of the macros which might be printed in serde_derive.
If there may be implementation work wanted in some construct instruments to accommodate it, somebody ought to be happy to try this work (as I’ve carried out for Buck and Bazel, that are instruments I take advantage of and contribute considerably to) or publish your personal fork of the supply code beneath a distinct identify.
Individually, relating to the commentary above about safety, the very best path ahead can be for one of many individuals who cares about this to put money into a Cargo or crates.io RFC round first-class precompiled macros so that there’s an method that will fit your preferences; serde_derive would undertake that when accessible.”
BleepingComputer has approached Tolnay with further questions previous to publishing.
“First .NET’s Moq and now this.”
Some Rust builders request that precompiled binaries be stored elective and separate from the unique “serde_derive” crate, whereas others have likened the transfer to the controversial code change to the Moq .NET challenge that sparked backlash.
“Please think about transferring the precompiled serde_derive model to a distinct crate and default serde_derive to constructing from supply in order that customers that need the good thing about precompiled binary can opt-in to make use of it,” requested one consumer.
“Or vice-versa. Or every other answer that permits constructing from supply with out having to patch serde_derive.”
“Having a binary shipped as a part of the crate, whereas I perceive the construct time pace advantages, is for safety causes not a viable answer for some library customers.”
Customers identified how the change may impression entities which might be “legally not allowed to redistribute pre-compiled binaries, by their very own licenses,” particularly mentioning government-regulated environments.
“…First .NET’s Moq and now this,” mentioned Jordan Singh, an Australia-based developer, in a remark that was later eliminated.
“If that is to pressure cargo devs to assist a characteristic then that is horrible approach round doing it. At-least give us reproducible binaries. I am sick of devs of in style crates/libraries taking everybody hostage with absurd choices.”
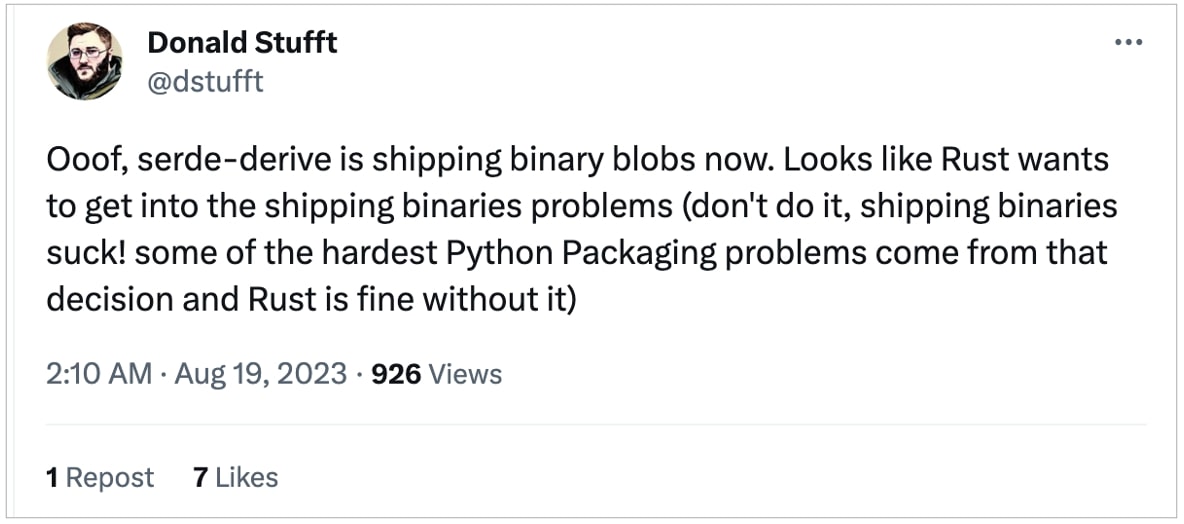
Philadelphia-based Donald Stufft cautioned in opposition to the dangers of stepping into the enterprise of “delivery binaries” on social media:
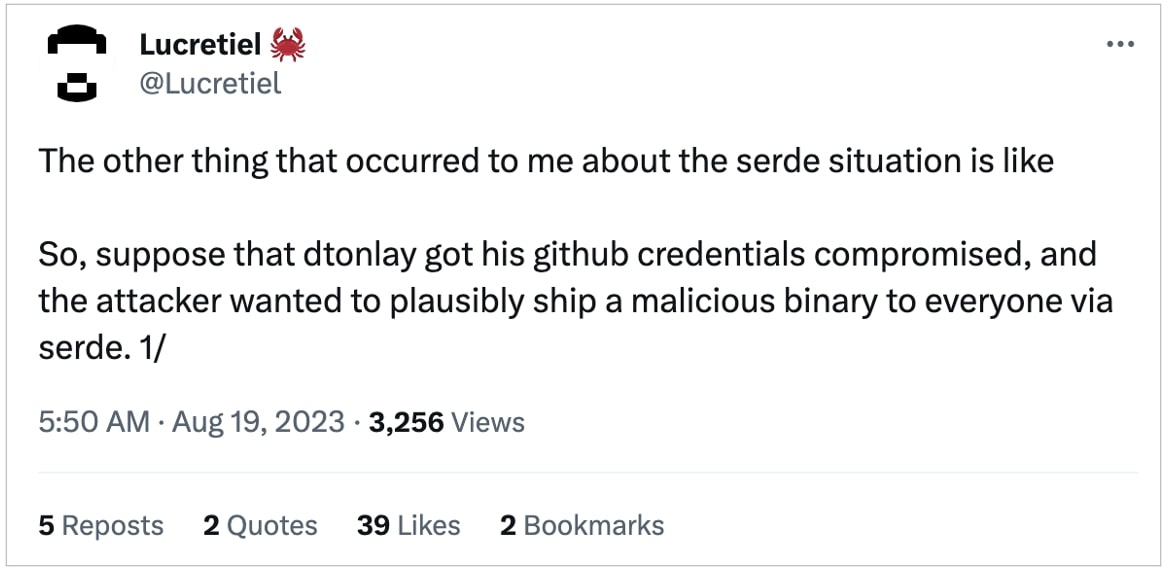
Rust programmer Nathan West, who goes by Lucretiel, particularly highlighted the supply-chain dangers posed by precompiled binaries, ought to the maintainer account get compromised:
“Shouldn’t be this the precise approach they’d go about it? Ship it silently as a semi-plausible change to how serde works, intransigently ignore all criticism of the choice,” wrote West.
“That is *precisely* the rationale that everybody has such a reflexive opposition to strikes like this.”
“Belief on the web is not excellent; we *do not* know that that is actually [the maintainer] posting in GitHub. That is why now we have layers and proxies of protection; sketchy sh*t is rejected as a result of it isn’t definitely worth the threat.
Technologist Sanket Kanjalkar referred to as the transition to ship binaries and not using a approach of opting-out “a step backward.”
However, a safety skilled who goes by Lander, has a barely totally different take:
“This Rust drama about serde_derive delivery a precompiled binary is type of humorous,” writes Lander.
“On one hand, I perceive folks’s concern. Alternatively, who cares? no one’s studying proc macro code/construct.rs code for each challenge they pull in anyhow. An opt-out can be a good suggestion tho.”
Whether or not you agree with the challenge’s choice to serve its macros precompiled or not, it’s a good apply to routinely examine any supply code and software program binaries prior to incorporating these into your tasks.
Because of Michael Kearns for the tip off.
