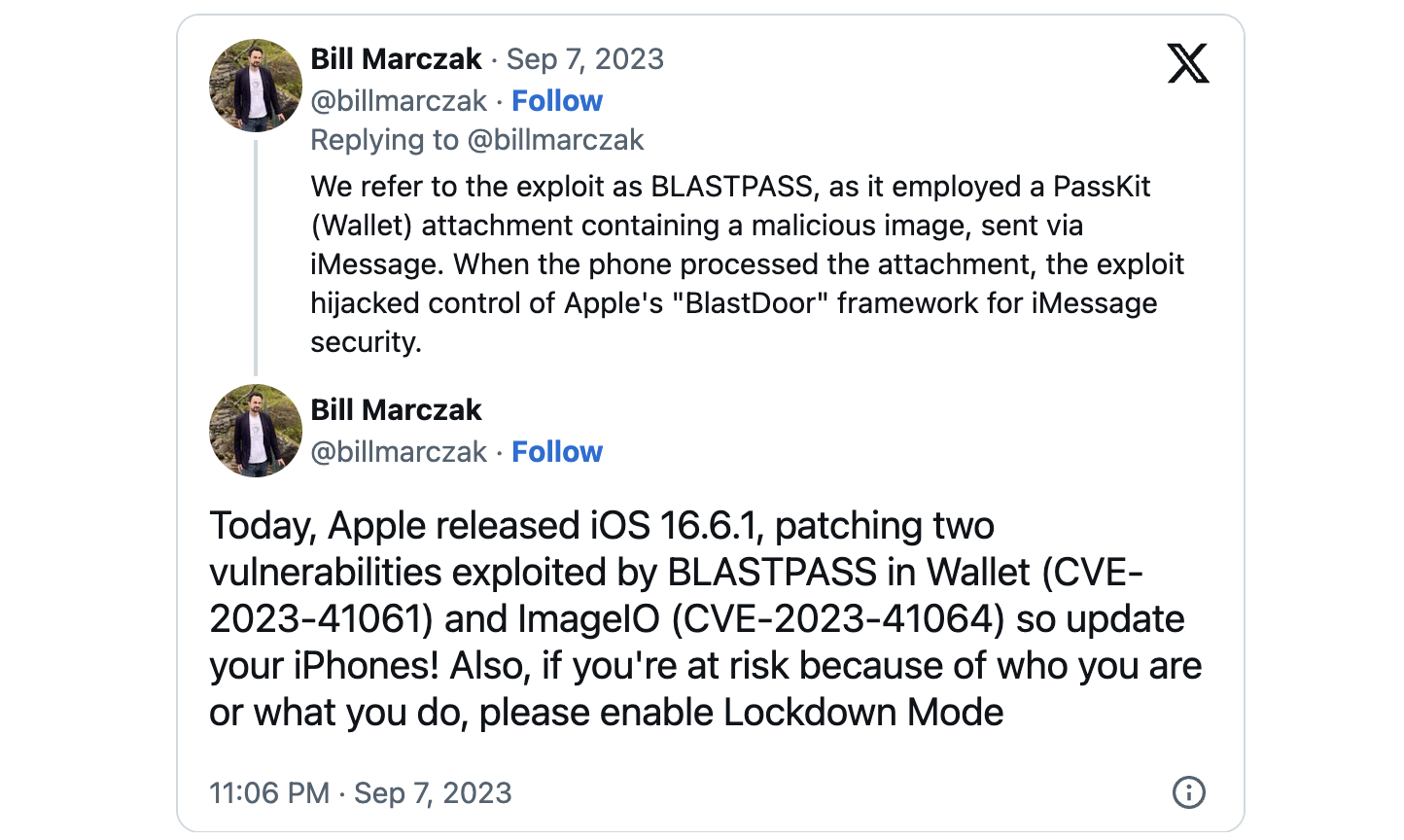
Citizen Lab says two zero-days mounted by Apple right now in emergency safety updates had been actively abused as a part of a zero-click exploit chain to deploy NSO Group’s Pegasus business spyware and adware onto absolutely patched iPhones.
The 2 bugs, tracked as CVE-2023-41064 and CVE-2023-41061, allowed the attackers to contaminate a fully-patched iPhone working iOS 16.6 and belonging to a Washington DC-based civil society group through PassKit attachments containing malicious photographs.
“We seek advice from the exploit chain as BLASTPASS. The exploit chain was able to compromising iPhones working the newest model of iOS (16.6) with none interplay from the sufferer,” Citizen Lab stated.
“The exploit concerned PassKit attachments containing malicious photographs despatched from an attacker iMessage account to the sufferer.”
Citizen Lab additionally urged Apple clients to replace their units instantly and inspired these vulnerable to focused assaults attributable to their id or occupation to activate Lockdown Mode.
Apple and Citizen Lab safety researchers found the 2 zero-days within the Picture I/O and Pockets frameworks.
CVE-2023-41064 is a buffer overflow triggered when processing maliciously crafted photographs, whereas CVE-2023-41061 is a validation challenge that may be exploited through malicious attachments.
Each permit menace actors to achieve arbitrary code execution on unpatched iPhone and iPad units.
Apple addressed the issues in macOS Ventura 13.5.2, iOS 16.6.1, iPadOS 16.6.1, and watchOS 9.6.2 with improved logic and reminiscence dealing with.
The listing of affected units contains:
- iPhone 8 and later
- iPad Professional (all fashions), iPad Air third era and later, iPad fifth era and later, and iPad mini fifth era and later
- Macs working macOS Ventura
- Apple Watch Collection 4 and later
For the reason that begin of the 12 months, Apple has mounted a complete of 13 zero-days exploited to focus on units working iOS, macOS, iPadOS, and watchOS, together with: