
The ‘ClearFake’ pretend browser replace marketing campaign has expanded to macOS, focusing on Apple computer systems with Atomic Stealer (AMOS) malware.
The ClearFake marketing campaign began in July this yr to focus on Home windows customers with pretend Chrome replace prompts that seem on breached websites through JavaScript injections.
In October 2023, Guardio Labs found a big growth for the malicious operation, which leveraged Binance Sensible Chain contracts to cover its malicious scripts supporting the an infection chain within the blockchain.
Through this system, dubbed “EtherHiding,” the operators distributed Home windows-targeting payloads, together with information-stealing malware like RedLine, Amadey, and Lumma.
Increasing to macOS
On November 17, 2023, risk analyst Ankit Anubhav reported that ClearFake had began pushing DMG payloads to macOS customers visiting compromised web sites.
A Malwarebytes report from earlier this week confirms this growth, reporting that these assaults make use of a Safari replace bait together with the usual Chrome overlay.
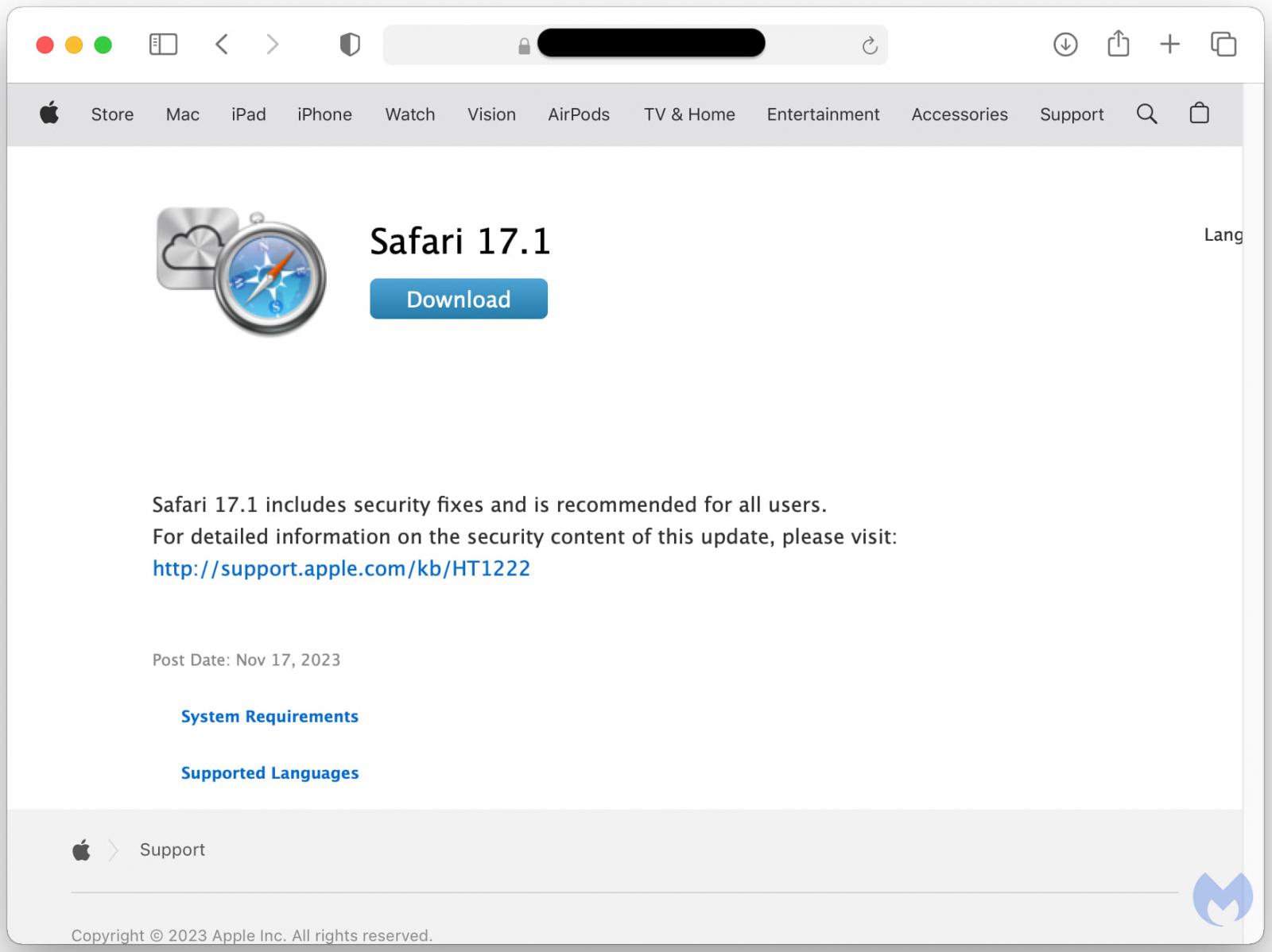
Supply: Malwarebytes
The payload dropped in these instances is Atomic, an info-stealing malware bought to cybercriminals through Telegram channels for $1,000/month.
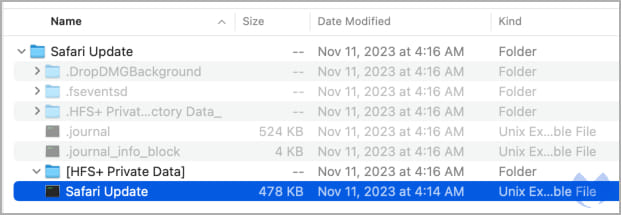
Supply: Malwarebytes
Atomic was found in April 2023 by Trellix and Cyble, who reported that it makes an attempt to steal passwords, cookies, and bank cards saved in browsers, native recordsdata, information from over 50 cryptocurrency extensions, and keychain passwords.
The keychain password is macOS’ built-in password supervisor that holds WiFi passwords, web site logins, bank card information, and different encrypted info, so its compromise may end up in a big breach for the sufferer.
Malwarebyte’s examination of the payload’s strings reveals a collection of instructions for extracting delicate information like passwords and focusing on doc recordsdata, photographs, crypto pockets recordsdata, and keys.
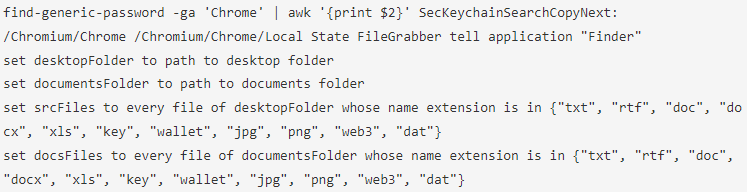
Supply: Malwarebytes
The ClearFake marketing campaign now focusing on Macs is a reminder for Apple customers to strengthen their safety and watch out with downloads, particularly prompts to replace your browser when visiting web sites.
Even after a number of months following the invention and experiences on Atomic, the payload is undetected by roughly 50% of AV engines on VirusTotal.
Moreover, all Safari browser updates can be distributed by means of macOS’s Software program Replace, or for different browsers, throughout the browser itself.
Due to this fact, in the event you see any prompts to obtain browser updates on web sites, they need to be ignored.
