Excessive severity vulnerability was found within the Elementor web site builder plugin that might permit an attacker to add recordsdata to the web site server and execute them. The vulnerability is within the template uploader performance.
Elementor Unrestricted Add of File with Harmful Sort Vulnerability
Elementor web site builder is a well-liked WordPress plugin with over 5 million installations. The recognition is pushed by its easy to make use of drag and drop performance for creating skilled wanting web sites.
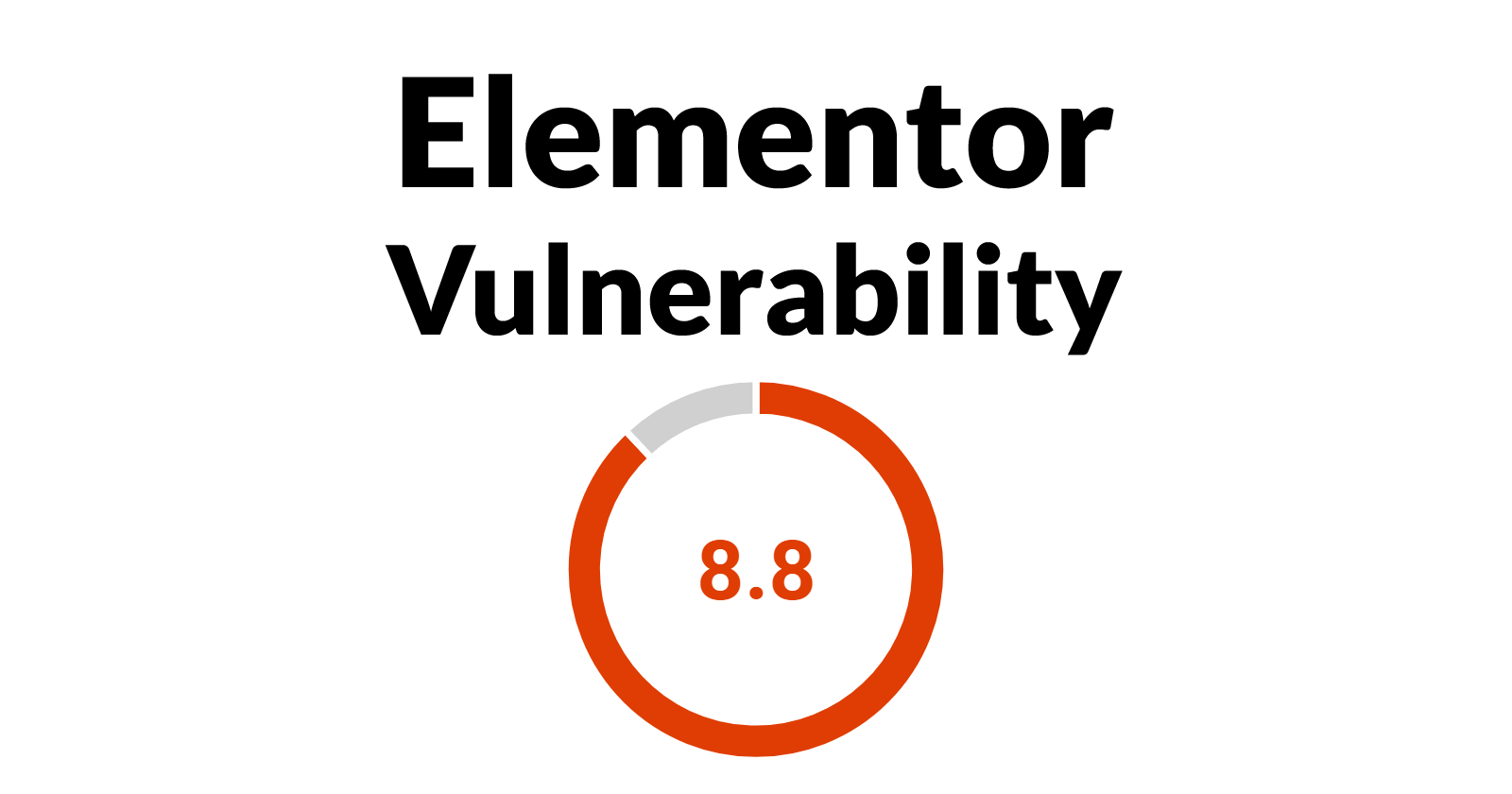
The vulnerability found in Elementor is rated 8.8/10 and is claimed to make web sites utilizing Elementor open to a Distant Code Execution whereby an attacker is ready to primarily management the affected web site and run varied instructions.
The kind of vulnerability is described as an Unrestricted Add of File with Harmful Sort. This sort of vulnerability is an exploit the place an attacker is ready to add malicious recordsdata which in flip permits the attacker to execute instructions on the affected web site server.
This sort of subject is typically described on this method:
“The product permits the attacker to add or switch recordsdata of harmful varieties that may be routinely processed inside the product’s atmosphere.”
Wordfence describes this particular vulnerability:
“The Elementor Web site Builder …plugin for WordPress is susceptible to Distant Code Execution by way of file add in all variations as much as and together with 3.18.0 by way of the template import performance.
This makes it doable for authenticated attackers, with contributor-level entry and above, to add recordsdata and execute code on the server.”
Wordfence additionally signifies that there isn’t any patch to repair this subject and recommends uninstalling Elementor.
“No identified patch out there. Please evaluation the vulnerability’s particulars in depth and make use of mitigations primarily based in your group’s danger tolerance. It might be finest to uninstall the affected software program and discover a substitute.”
Elementor 3.18.1 Model Replace
Elementor launched an replace to model 3.18.1 right now. It’s unclear if this patch fixes the vulnerability because the Wordfence website presently states that the vulnerability is unpatched.
The changelog describes this replace:
“Repair: Improved code safety enforcement in File Add mechanism”
It is a newly reported vulnerability and the information might change. Wordfence nevertheless warns that hackers are already attacking Elementor web sites as a result of their paid model has already blocked eleven hacking makes an attempt on the time of publishing the announcement.
Learn the Wordfence advisory: