
A proof-of-concept exploit was publicly launched for a crucial distant code execution vulnerability within the CrushFTP enterprise suite, permitting unauthenticated attackers to entry information on the server, execute code, and acquire plain-text passwords.
The vulnerability was found in August 2023, tracked as CVE-2023-43177, by Converge safety researchers, who responsibly reported it to the seller. The builders launched a repair in a single day in model CrushFTP 10.5.2.
At this time, Converge revealed a proof-of-concept exploit for the CVE-2023-43177 flaw, making it crucial for CrushFTP customers to put in the safety updates as quickly as doable.
Exploiting CrushFTP
The CrushFTP exploit is performed by an unauthenticated mass-assignment vulnerability, exploiting the AS2 header parsing to manage person session properties.
This enables attackers to learn and delete information, doubtlessly main to finish system management and root-level distant code execution.
The attackers can ship payloads to the CrushFTP service on particular ports (80, 443, 8080, 9090) utilizing internet headers, which go away log traces.
Subsequent, the attackers overwrite session information utilizing Java’s ‘putAll()’ operate, enabling the impersonation of ‘directors,’ and leverage the ‘drain_log()’ operate to govern information as wanted to keep up stealthiness.
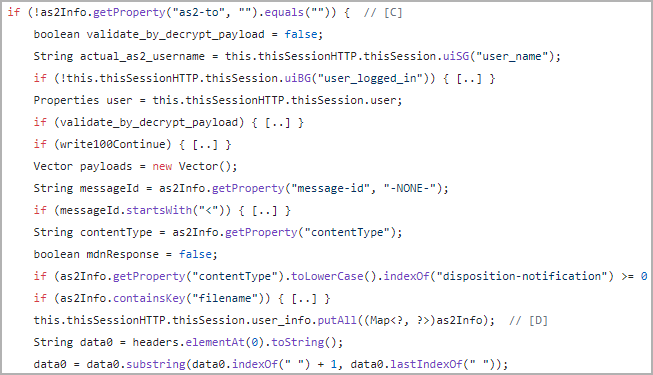
Ultimately, the attackers can leverage the ‘periods. obj’ file in this system’s set up folder to hijack dwell person periods belonging to admin accounts, primarily reaching privileged escalation.
Having established admin entry, the attacker can exploit flaws within the admin panel’s dealing with of SQL driver loading and database configuration testing (testDB) to execute arbitrary Java code.
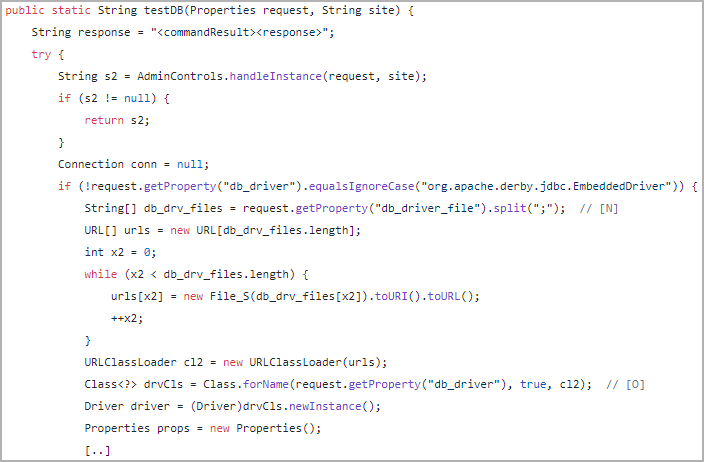
Converge has revealed an indication of the video of the PoC exploit in use, as proven beneath.
1000’s of weak units
In accordance with Converge’s report, there are roughly 10,000 public-facing CrushFTP situations and certain many extra behind company firewalls. The assault floor is sizable regardless that the variety of weak situations hasn’t been decided.
File switch merchandise like CrushFTP are notably engaging to ransomware actors, particularly Clop, identified for leveraging zero-day vulnerabilities in software program just like the MOVEit Switch, GoAnywhere MFT, and Accelion FTA to conduct information theft assaults.
Sadly, the researchers revealed that even making use of the patches does not safe CrushFTP endpoints in opposition to all doable threats.
“Converge’s menace intelligence signifies that the safety patch has been reverse-engineered, and adversaries have developed proofs of ideas. Due to that, upcoming exploitation is probably going.” – Converge
To successfully mitigate the danger, it is strongly recommended to comply with these steps:
- Replace CrushFTP to the most recent model.
- Allow automated safety patch updates.
- Change the password algorithm to Argon.
- Audit for unauthorized customers and examine for current password modifications.
- Activate the brand new Restricted Server mode for enhanced safety.
Extra measures that may be carried out to boost CrushFTP safety additional embrace:
- Utilizing a restricted privilege working system service account for CrushFTP.
- Deploying Nginx or Apache as a reverse proxy for public-facing servers.
- Setting firewall guidelines to restrict CrushFTP visitors to trusted IP ranges and hosts.
It is important to implement these safety measures as quickly as doable, because the publicly disclosed exploit particulars of CVE-2023-43177 are doubtless for use by hackers in opportunistic assaults.
