
The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Safety Company launched an advisory in regards to the evasive risk actor tracked as Scattered Spider, a loosely knit hacking collective that now collaborates with the ALPHV/BlackCat Russian ransomware operation.
Scattered Spider, often known as 0ktapus, Starfraud, UNC3944, Scatter Swine, Octo Tempest, and Muddled Libra, is adept at social engineering and depends on phishing, multi-factor authentication (MFA) bombing (focused MFA fatigue), and SIM swapping to realize preliminary community entry on massive organizations.
The group contains younger English-speaking members (as younger as 16) with various talent units who frequent the identical hacker boards and Telegram channels.
A number of the members are believed to even be a part of the “Comm” – a loose-knit neighborhood concerned in violent acts and cyber incidents that has been gaining vast media consideration currently.
Opposite to the overall perception that it’s a cohesive gang, they’re a community of people, with completely different risk actors collaborating in every assault. This fluid construction is what makes it troublesome to trace them.
Nonetheless, in response to Reuters journalists, the FBI is aware of the identities of not less than 12 members of the group however none have been indicted or arrested but.
Background
Scattered Spider assaults have been documented since final summer time when researchers at cybersecurity firm Group-IB publishing a report a couple of spree of assaults aiming to steal Okta identification credentials and 2FA codes, which had began March the identical yr.
In December 2022, CrowdStrike profiled the risk actor as a financially motivated group concentrating on telcos, using high-level social engineering techniques, protection reversal, and a wealthy set of software program instruments.
In January 2023, Crowdstrike found that Scattered Spider was utilizing BYOVD (Convey Your Personal Weak Driver) strategies to evade detection from EDR (endpoint detection and response) safety merchandise.
Extra just lately, in September this yr, to 2 high-profile assaults towards MGM On line casino and Caesars Leisure, have been attributed to Scattered Spider, the place the risk actors used the BlackCat/ALPHV locker to encrypt programs.
Previous exercise from the risk actor contains assaults on MailChimp, Twilio, DoorDash, and Riot Video games.
An October report by Microsoft, who calls them Octo Tempest, says that they’re one of the vital harmful monetary felony teams, and have been recognized to resort to violent threats to attain their objectives.
supply: Microsoft
The researchers’ findings in regards to the group’s number of assault strategies point out that its members have data that extends to completely different areas of cybercrime, from social engineering and hacking, to SIM swapping, phishing, and bypassing login protections.
Scattered Spider techniques
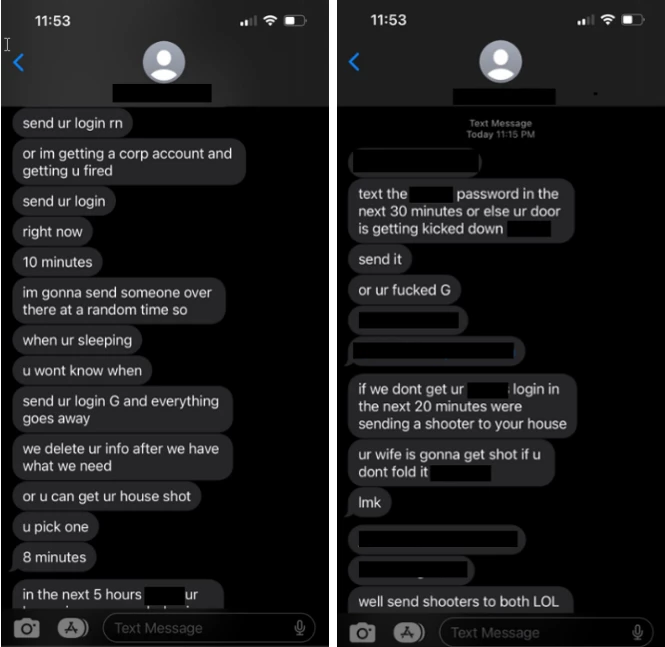
The FBI and CISA alert highlights Scattered Spider’s highly effective preliminary entry techniques that contain concentrating on an organization’s staff by posing as IT or help-desk workers and tricking them into offering credentials and even direct community entry.
Particular person techniques embody cellphone calls, SMS phishing, electronic mail phishing, MFA fatigue assaults, and SIM swapping. The domains used for electronic mail and SMS phishing abuse the Okta and Zoho ServiceDesk manufacturers mixed with the goal’s title to make them seem respectable.
After establishing a foothold on the community, Scattered Spider makes use of a variety of publicly obtainable software program instruments for reconnaissance and lateral motion, together with:
- Fleetdeck.io: Distant system monitoring and administration
- Stage.io: Distant system monitoring and administration
- Mimikatz: Credential extraction
- Ngrok: Distant internet server entry through web tunneling
- Pulseway: Distant system monitoring and administration
- Screenconnect: Community system distant connection administration
- Splashtop: Community system distant connection administration
- Tactical.RMM: Distant system monitoring and administration
- Tailscale: VPN for safe community communications
- Teamviewer: Community system distant connection administration
Other than the above respectable instruments used for malicious functions, Scattered Spider additionally conducts phishing assaults to put in malware just like the WarZone RAT, Raccoon Stealer, and Vidar Stealer, to steal from compromised programs login credentials, cookies, and different knowledge helpful within the assault.
A brand new tactic noticed within the risk group’s latest assaults is knowledge exfiltration and file encryption utilizing the ALPHV/BlackCat ransomware, adopted by communication with the victims through a messaging app, electronic mail, or different safe instruments to barter a ransom cost.
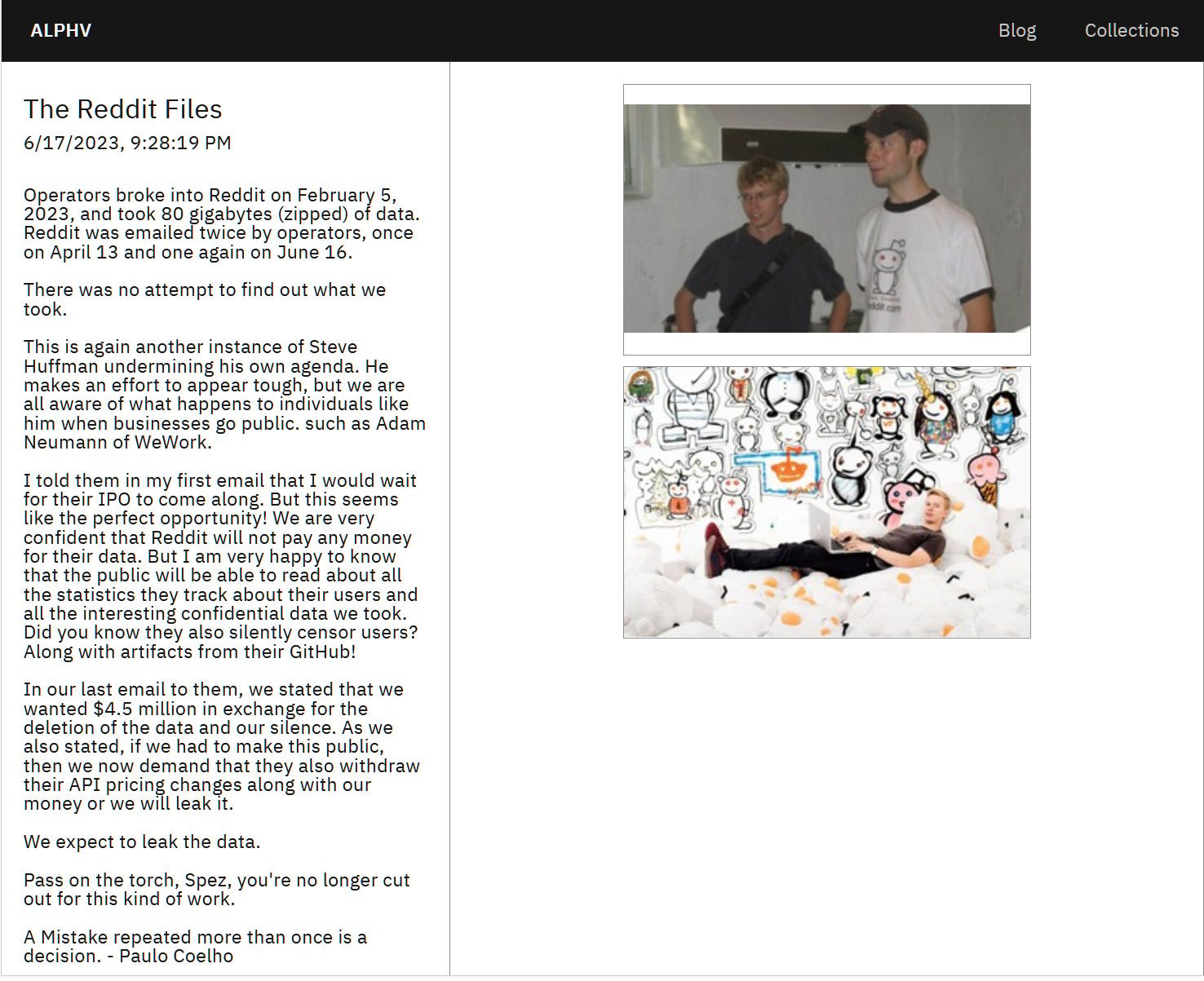
The Scattered Spider actors affiliated with BlackCat are additionally recognized to make use of the ransomware gang’s knowledge leak website as a part of their extortion makes an attempt, the place they leak knowledge or difficulty statements, because it occurred with their assault on Reddit.
supply: BleepingComputer
Scattered Spider reveals explicit curiosity in priceless property like supply code repositories, code-signing certificates, and credential storage.
Additionally, the attackers carefully monitor the sufferer’s Slack channels, Microsoft Groups, and Microsoft Change emails for messages containing any indication that their actions have been found.
“The risk actors incessantly be part of incident remediation and response calls and teleconferences, more likely to establish how safety groups are looking them and proactively develop new avenues of intrusion in response to sufferer defenses” – Federal Bureau of Investigation
The company provides that the cybercriminals obtain this “by creating new identities within the atmosphere” that always have pretend social media profiles for a false sense of legitimacy.
Proposed mitigations
The FBI and CISA suggest implementing particular mitigations to guard towards threats imposed by Scattered Spider.
Key suggestions within the advisory suggest to:
- Use software controls with “allowlisting” to handle software program execution.
- Monitor distant entry instruments and implement phishing-resistant multifactor authentication (MFA).
- Safe and restrict Distant Desktop Protocol (RDP) utilization with finest practices and MFA.
- Preserve offline backups and cling to a sturdy knowledge restoration plan.
- Comply with NIST requirements for sturdy, much less incessantly modified passwords.
- Hold programs and software program frequently up to date, specializing in patching vulnerabilities.
- Implement community segmentation to regulate site visitors and forestall ransomware unfold.
- Use community monitoring and Endpoint Detection and Response (EDR) instruments to detect irregular actions.
- Improve electronic mail safety by disabling dangerous hyperlinks and encrypting backup knowledge.
Lastly, organizations are suggested to check and validate their safety controls towards MITRE ATT&CK strategies described within the advisory.
