Google has patched the fifth Chrome zero-day vulnerability exploited in assaults because the begin of the 12 months in emergency safety updates launched at this time.
“Google is conscious that an exploit for CVE-2023-5217 exists within the wild,” the corporate revealed in a safety advisory revealed on Wednesday.
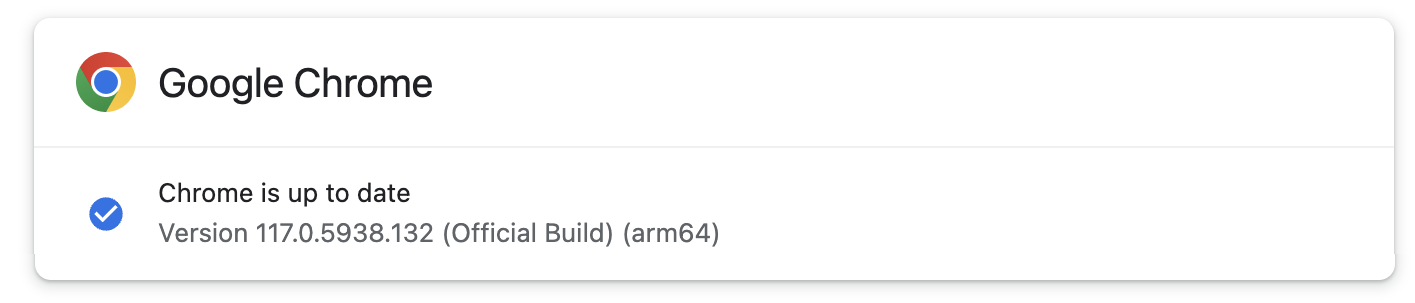
The safety vulnerability is addressed in Google Chrome 117.0.5938.132, rolling out worldwide to Home windows, Mac, and Linux customers within the Secure Desktop channel.
Whereas the advisory says it’s going to possible take days or perhaps weeks till the patched model reaches the complete person base, the replace was instantly out there when BleepingComputer checked for updates.
The online browser may even auto-check for brand spanking new updates and robotically set up them after the subsequent launch.
Exploited in adware assaults
The high-severity zero-day vulnerability (CVE-2023-5217) is attributable to a heap buffer overflow weak point within the VP8 encoding of the open-source libvpx video codec library, a flaw whose affect ranges from app crashes to arbitrary code execution.
The bug was reported by Google Menace Evaluation Group (TAG) safety researcher Clément Lecigne on Monday, September 25.
Google TAG researchers are identified for sometimes discovering and reporting zero-days abused in focused adware assaults by government-sponsored risk actors and hacking teams concentrating on high-risk people resembling journalists and opposition politicians.
At this time, Google TAG’s Maddie Stone revealed that the CVE-2023-5217 zero-day vulnerability was exploited to put in adware.
With Citizen Lab researchers, Google TAG additionally disclosed on Friday that three zero-days patched by Apple final Thursday had been used to set up Cytrox’s Predator adware between Could and September 2023.
Though Google mentioned at this time that the CVE-2023-5217 zero-day had been exploited in assaults, the corporate has but to share extra data relating to these incidents.
“Entry to bug particulars and hyperlinks could also be saved restricted till a majority of customers are up to date with a repair,” Google mentioned. “We may even retain restrictions if the bug exists in a 3rd celebration library that different initiatives equally rely upon, however have not but fastened.”
As a direct end result, Google Chrome customers can have sufficient time to replace their browsers as a preemptive measure in opposition to potential assaults.
This proactive strategy can assist mitigate the chance of risk actors creating their very own exploits and deploying them in real-world situations, notably as extra technical particulars grow to be out there.
Google fastened one other zero-day (tracked as CVE-2023-4863) exploited within the wild two weeks in the past, the fourth one because the begin of the 12 months.
Whereas first marking it as a Chrome flaw, the corporate later assigned one other CVE (CVE-2023-5129) and a most 10/10 severity score, tagging it as a essential safety vulnerability in libwebp (a library utilized by numerous initiatives, together with Sign, 1Password, Mozilla Firefox, Microsoft Edge, Apple’s Safari, and the native Android net browser).