
Hackers are conducting widespread exploitation of a crucial WooCommerce Funds plugin to realize the privileges of any customers, together with directors, on weak WordPress set up.
WooCommerce Funds is a highly regarded WordPress plugin permitting web sites to simply accept credit score and debit playing cards as fee in WooCommerce shops. In accordance with WordPress, the plugin is used on over 600,000 lively installations.
On March twenty third, 2023, the builders launched model 5.6.2 to repair the crucial 9.8-rated vulnerability tracked as CVE-2023-28121. The flaw impacts WooCommerce Fee plugin variations 4.8.0 and better, with it being fastened in variations 4.8.2, 4.9.1, 5.0.4, 5.1.3, 5.2.2, 5.3.1, 5.4.1, 5.5.2, 5.6.2, and later.
Because the vulnerability permits any distant person to impersonate an administrator and take full management over a WordPress website, Automattic pressure put in the safety repair of WordPress installations using the plugin.
On the time, WooCommerce mentioned there was no identified lively exploitation of the vulnerability, however researchers warned that as a result of crucial nature of the bug, we might probably see exploitation sooner or later.
Flaw actively exploited
This month, researchers at RCE Safety analyzed the bug and launched a technical weblog on the CVE-2023-28121 vulnerability and the way it may be exploited.
The researchers clarify that attackers can merely add an ‘X-WCPAY-PLATFORM-CHECKOUT-USER‘ request header and set it to the person ID of the account they want to impersonate.
When WooCommerce Funds sees this header, it should deal with the request as if it was from the required person ID, together with all the person’s privileges.
As a part of the weblog put up, RCE Safety launched a proof-of-concept exploit that makes use of this flaw to create a brand new admin person on weak WordPress websites, making it straightforward for risk actors to take full management over the positioning.
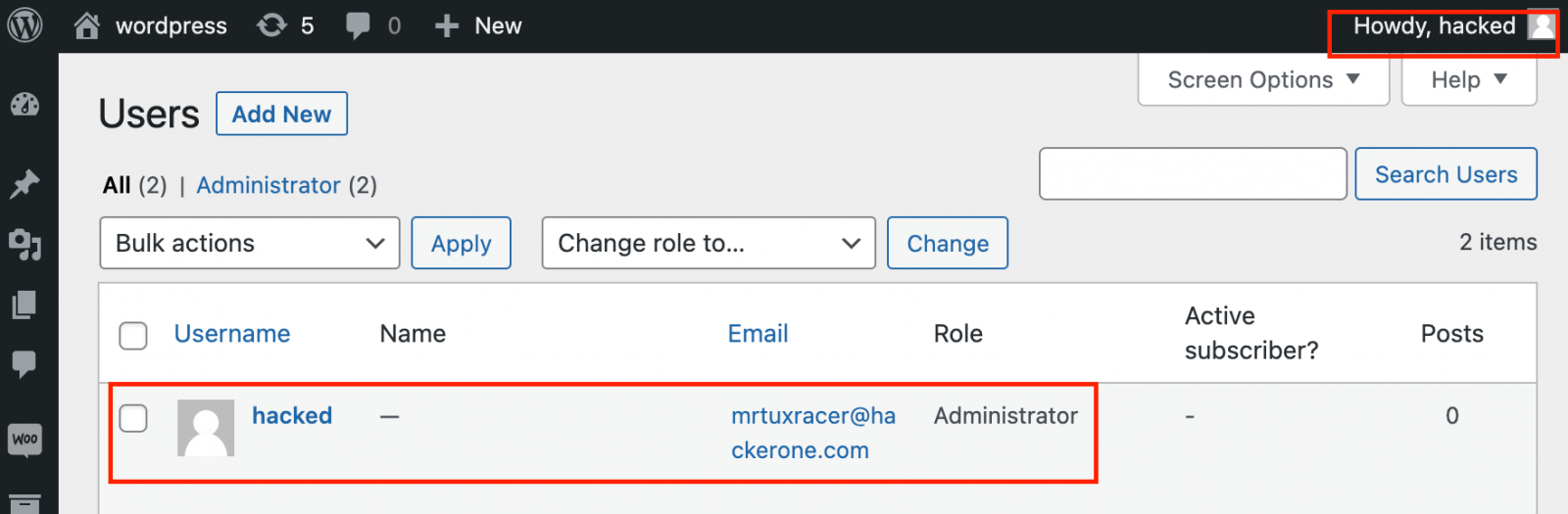
Supply: RCE Safety
At present, WordPress safety agency Wordfence warned that risk actors are exploiting this vulnerability in an enormous marketing campaign concentrating on over 157,000 websites by Saturday.
“Massive-scale assaults towards the vulnerability, assigned CVE-2023-28121, started on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million assaults towards 157,000 websites on Saturday, July 16, 2023,” explains Wordfence.
Wordfence says the risk actors use the exploit to put in the WP Console plugin or create administrator accounts on the focused machine.
For these techniques that WP Console was put in, the risk actors used the plugin to execute PHP code that installs a file uploader on the server that can be utilized as a backdoor even after the vulnerability is fastened.?
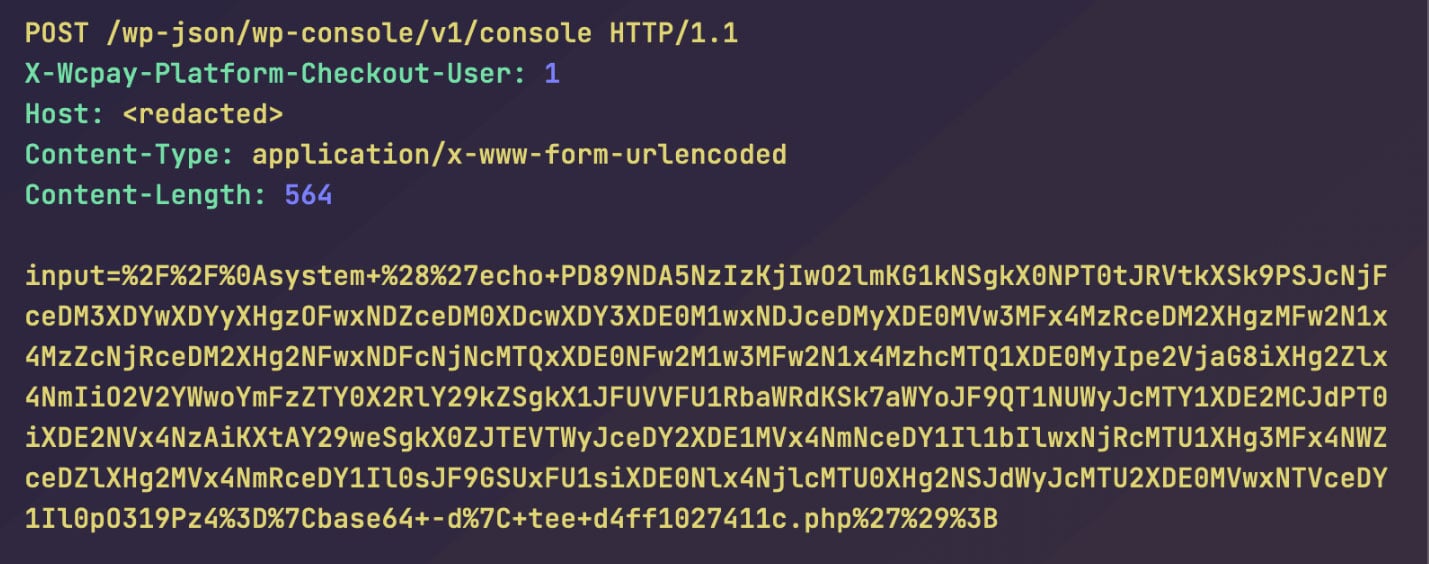
Supply: Wordfence
Wordfence says they’ve seen different attackers utilizing the exploit to create administrator accounts with random passwords.
To scan for weak WordPress websites, the risk actors attempt to entry the ‘/wp-content/plugins/woocommerce-payments/readme.txt’ file, and if it exists, they exploit the flaw.
The researchers have shared seven IP addresses accountable for these assaults, with IP handle 194.169.175.93 scanning 213,212 websites.
BleepingComputer has seen related exercise in our entry logs, beginning on July twelfth.
As a result of ease with which CVE-2023-28121 could be exploited, it’s strongly suggested that each one websites using the WooCommerce Fee plugin be certain that their installations are up-to-date.
When you’ve got not up to date your set up not too long ago, it is usually suggested that website admins scan their websites for uncommon PHP recordsdata and suspicious administrator accounts and delete any which can be discovered.
