
Microsoft mounted a safety flaw within the Energy Platform Customized Connectors characteristic that allow unauthenticated attackers entry cross-tenant functions and Azure clients’ delicate knowledge after being referred to as “grossly irresponsible” by Tenable’s CEO.
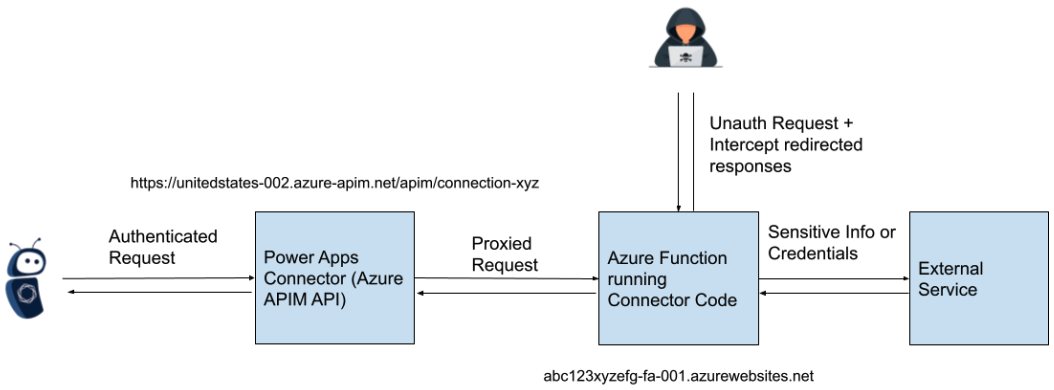
The basis reason for the difficulty stemmed from insufficient entry management measures for Azure Operate hosts launched by connectors inside the Energy Platform. These connectors use customized C# code built-in right into a Microsoft-managed Azure Operate that includes an HTTP set off.
Though buyer interplay with customized connectors normally occurs through authenticated APIs, the API endpoints facilitated requests to the Azure Operate with out implementing authentication.
This created a chance for attackers to use unsecured Azure Operate hosts and intercept OAuth shopper IDs and secrets and techniques.
“It must be famous that this isn’t completely a difficulty of knowledge disclosure, as having the ability to entry and work together with the unsecured Operate hosts, and set off conduct outlined by customized connector code, may have additional impression,” says cybersecurity agency Tenable which found the flaw and reported it on March thirtieth.
“Nevertheless, due to the character of the service, the impression would fluctuate for every particular person connector, and can be troublesome to quantify with out exhaustive testing.”
“To offer you an thought of how dangerous that is, our group in a short time found authentication secrets and techniques to a financial institution. They had been so involved in regards to the seriousness and the ethics of the difficulty that we instantly notified Microsoft,” Tenable CEO Amit Yoran added.
Tenable additionally shared proof of idea exploit code and data on the steps required to search out susceptible connector hostnames and how one can craft the POST requests to work together with the unsecured API endpoints.
Whereas investigating Tenable’s report, the corporate initially discovered that the researcher was the one one who exploited the difficulty. After additional evaluation in July, Microsoft decided that there have been some Azure Capabilities in a “mushy delete” state that had not been correctly mitigated.
Microsoft lastly resolved the difficulty for all clients on August 2nd after an preliminary repair deployed by Redmond on June seventh was tagged by Tenable as incomplete.
“This concern has been totally addressed for all clients and no buyer remediation motion is required,” Microsoft mentioned on Friday.
Redmond has since notified all impacted clients by means of the Microsoft 365 Admin Middle beginning August 4th.
Though Microsoft says the knowledge disclosure concern was addressed for all Azure clients, Tenable believes the repair applies solely to newly deployed Energy Apps and Energy Automation customized connectors.
“Microsoft has mounted the difficulty for newly deployed connectors by requiring Azure Operate keys to entry the Operate hosts and their HTTP set off,” Tenable says.
“We’d refer clients who require further particulars relating to the character of the deployed remediations to Microsoft for authoritative solutions.”
Repair solely got here after public criticism
Microsoft addressed the flaw after a five-month interval, however not earlier than the CEO of Tenable voiced vehement criticism towards the preliminary response. Yoran condemned Microsoft’s strategy as “grossly irresponsible” and “blatantly negligent.”
To make issues even worse, Redmond’s preliminary dedication to fixing the difficulty in September deviated by a big margin from the anticipated 90-day deadline, sometimes adhered to by most distributors in terms of patching safety vulnerabilities.
This prolonged delay added to the issues and raised further questions in regards to the timeliness of Microsoft’s response to safety points affecting discovered inside its merchandise.
“Did Microsoft shortly repair the difficulty that would successfully result in the breach of a number of clients’ networks and providers? After all not. They took greater than 90 days to implement a partial repair – and just for new functions loaded within the service,” Yoran mentioned.
“That implies that as of at present, the financial institution I referenced above continues to be susceptible, greater than 120 days since we reported the difficulty, as are all the different organizations that had launched the service previous to the repair.
“And, to the perfect of our data, they nonetheless do not know they’re in danger and subsequently can’t make an knowledgeable choice about compensating controls and different threat mitigating actions.”
