
MySQL servers are being focused by the ‘Ddostf’ malware botnet to enslave them for a DDoS-as-a-Service platform whose firepower is rented to different cybercriminals.
This marketing campaign was found by researchers on the AhnLab Safety Emergency Response Middle (ASEC) throughout their common monitoring of threats focusing on database servers.
ASEC stories that Ddostf’s operators both leverage vulnerabilities in unpatched MySQL environments or brute-force weak administrator account credentials to breach the servers.
Exploitation of UDF
The attackers are scanning the web for uncovered MySQL servers and, when discovered, try and breach them by brute-forcing administrator credentials.
For Home windows MySQL servers, the risk actors use a characteristic known as user-defined features (UDFs) to execute instructions on the breached system.
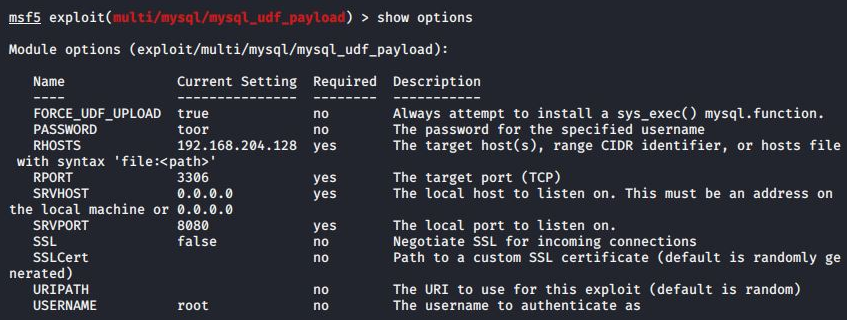
UDF is a MySQL characteristic that permits customers to outline features in C or C++ and compile them right into a DLL (dynamic hyperlink library) file that extends the capabilities of the database server.
The attackers, on this case, create their very own UDFs and register them with the database server as a DLL file (amd.dll) with the next malicious features:
- Downloading payloads just like the Ddostf DDoS bot from a distant server.
- Executing arbitrary system-level instructions despatched by the attackers.
- Output the outcomes of command execution to a short lived file and ship them to the attackers.
The UDF abuse facilitates loading the first payload of this assault, the Ddostf bot shopper.
Nevertheless, it may well additionally doubtlessly permit different malware set up, knowledge exfiltration, creation of backdoors for persistent entry, and extra.
Ddostf particulars
Ddostf is a malware botnet of Chinese language origin, first noticed within the wild roughly seven years in the past, and targets each Linux and Home windows methods.
On Home windows, it establishes persistence by registering itself as a system service upon first working after which decrypts its C2 (command and management) configuration to determine a connection.
The malware profiles the host system and sends knowledge similar to CPU frequency and variety of cores, language data, Home windows model, community velocity, and many others., to its C2.
The C2 server could ship DDoS assault instructions to the botnet shopper, together with SYN Flood, UDP Flood, and HTTP GET/POST Flood assault sorts, request to cease transmitting system standing data, swap to a brand new C2 deal with, or obtain and execute a brand new payload.
ASEC feedback that Ddostf’s capacity to connect with a brand new C2 deal with makes it stand out from most DDoS botnet malware and is a component that offers it resilience towards takedowns.
The cybersecurity firm means that MySQL admins apply the newest updates and choose lengthy, distinctive passwords to guard admin accounts from brute pressure and dictionary assaults.
