
Microsoft has printed an in depth profile of a local English-speaking risk actor with superior social engineering capabilities it tracks as Octo Tempest, that targets corporations in information extortion and ransomware assaults.
Octo Tempest’s assaults have steadily developed since early 2022, increasing their concentrating on to organizations offering cable telecommunications, electronic mail, and tech companies, and partnering with the ALPHV/BlackCat ransomware group.
From account theft to ransomware
The risk actor was initially noticed promoting SIM swaps and stealing accounts of high-profile people with cryptocurrency property.
In late 2022, Octa Tempest moved to phishing, social engineering, resetting passwords en-masse for the purchasers of breached service suppliers, and information theft.
Earlier this yr, the risk group attacked corporations within the gaming, hospitality, retail, manufacturing, expertise, and monetary sectors, in addition to managed service suppliers (MSPs).
After turning into an ALPHV/BlackCat affiliate, Octa Tempest deployed the ransomware each to steal and to encrypt sufferer information.
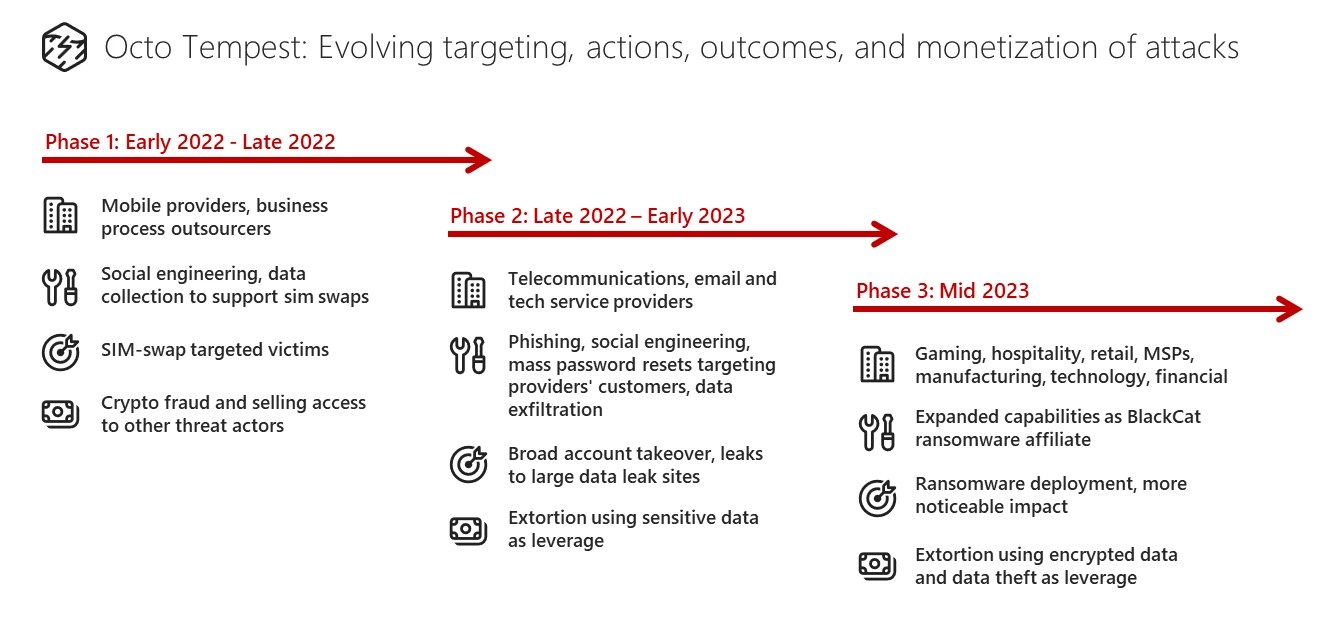
supply: Microsoft
The group used its amassed expertise to construct extra superior and aggressive assaults and in addition began to monetize intrusions by extorting victims after stealing information.
Microsoft says that Octo Tempest additionally used direct bodily threats in some instances to acquire logins that may advance their assault.
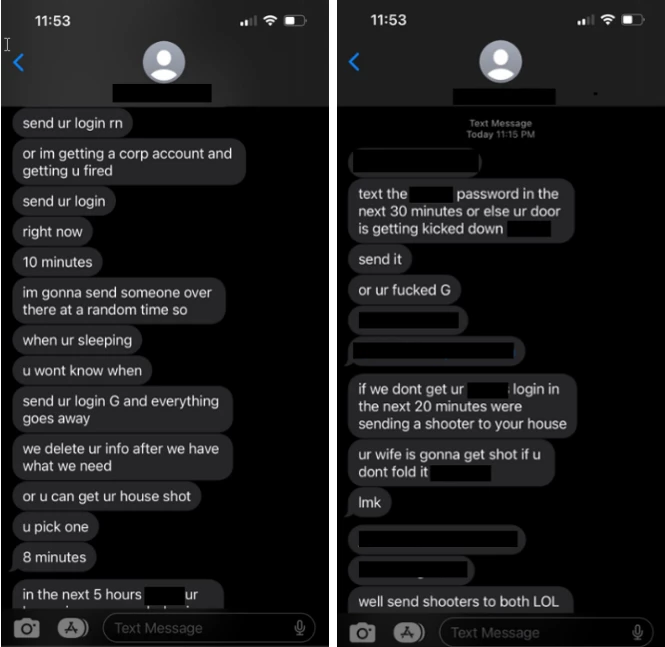
supply: Microsoft
In an odd flip of occasions, Octo Tempest turned an affiliate of the ALPHV/BlackCat ransomware-as-a-service (RaaS) operation, Microsoft says, and by June they began deploying each the Home windows and Linux ransomware payloads, specializing in VMware ESXi servers currently.
“That is notable in that, traditionally, Jap European ransomware teams refused to do enterprise with native English-speaking criminals” – Microsoft
The more moderen assaults from this group goal organizations in a wide range of sectors, together with gaming, pure assets, hospitality, client merchandise, retail, managed service suppliers, manufacturing, regulation, expertise, and monetary companies.
Octo Tempest TTPs
Microsoft assesses that Octo Tempest is a well-organized group that features members with intensive technical information and a number of hand-on-keyboard operators.
The hackers typically acquire preliminary entry via superior social engineering that targets accounts of technical directors (e.g. help and assist desk employees) with sufficient permissions to additional the assault.
They analysis the corporate to determine the targets they’ll impersonate to the extent of mimicking the speech patterns of the person in cellphone calls.
By doing so, they trick technical directors into performing password resets and reset multi-factor authentication (MFA) strategies.
Different strategies for preliminary entry embrace:
- tricking the goal into putting in distant monitoring and administration software program
- stealing the logins via phishing websites
- shopping for credentials or session tokens from different cybercriminals
- SMS phishing staff with hyperlinks to faux login portals that seize the credentials
- SIM-swapping or name forwarding
- Direct threats of violence
As soon as they get ample entry, Octo Tempest hackers begin the reconnaissance stage of the assault by enumerating hosts and companies and gathering info that may allow abusing reliable channels to progress the intrusion.
“Preliminary bulk-export of customers, teams, and gadget info is carefully adopted by enumerating information and assets available to the person’s profile inside digital desktop infrastructure or enterprise-hosted assets” – Microsoft
Octo Tempest then proceeds to discover the infrastructure, enumerating entry and assets throughout cloud environments, code repositories, server and backup administration techniques.
To escalate privileges, the risk actor once more turns to social engineering, SIM-swapping, or name forwarding, and initiates a self-service password reset of the goal’s account.
Throughout this step, the hackers construct belief with the sufferer by utilizing compromised accounts and demonstrating an understanding of the corporate’s procedures. If they’ve a supervisor’s account, they approve requests for elevated permissions themselves.
For so long as they’ve entry, Octo Tempest continues to search for further credentials to broaden their attain. They use instruments like Jercretz and TruffleHog to automate the seek for plaintext keys, secrets and techniques, and passwords throughout code repositories.
To maintain their tracks hidden, the hackers additionally goal the accounts of safety personnel, which permits them to disable safety merchandise and options.
“Utilizing compromised accounts, the risk actor leverages EDR and gadget administration applied sciences to permit malicious tooling, deploy RMM software program, take away or impair safety merchandise, information theft of delicate information (e.g. information with credentials, sign messaging databases, and many others.), and deploy malicious payloads” – Microsoft
In line with Microsoft, Octo Tempest tries to cover their presence on the community by suppressing alerts of modifications and modifying the mailbox guidelines to delete emails that would increase the sufferer’s suspicions of a breach.
The researchers present the next further instruments and methods that Octo Tempest makes use of of their assaults:
- open-source instruments: ScreenConnect, FleetDeck, AnyDesk, RustDesk, Splashtop, Pulseway, TightVNC, LummaC2, Stage.io, Mesh, TacticalRMM, Tailscale, Ngrok, WsTunnel, Rsocx, and Socat
- deploying Azure digital machines to allow distant entry through RMM set up or modification to present assets through Azure serial console
- including MFA strategies to present customers
- utilizing the tunneling instrument Twingate, which leverages Azure Container situations as a non-public connector (with out public community publicity)
The hackers additionally transfer stolen information to their servers utilizing a novel approach, which includes Azure Information Manufacturing facility and automatic pipelines to mix in with typical large information operations.
To export SharePoint doc libraries and switch the information faster, the attacker has been typically noticed to register reliable Microsoft 365 backup options reminiscent of Veeam, AFI Backup, and CommVault.
Microsoft notes that detecting or trying to find this risk actor in an surroundings will not be a simple activity resulting from the usage of social engineering, living-off-the-land methods, and the various tooling.
Nonetheless, the researchers present a set of normal tips that would assist detect malicious exercise, which begins with monitoring and reviewing identity-related processes, Azure environments, and endpoints.
Octo Tempest is financially motivated and achieves its objectives via stealing cryptocurrency, information theft extortion, or encrypting techniques and asking for a ransom.
