
Ransomware gangs goal uncovered Citrix Netscaler gadgets utilizing a publicly out there exploit to breach massive organizations, steal information, and encrypt recordsdata.
The menace actors exploit the Citrix Bleed vulnerability (CVE-2023-4966), which was disclosed final month and continues to be abused in assaults.
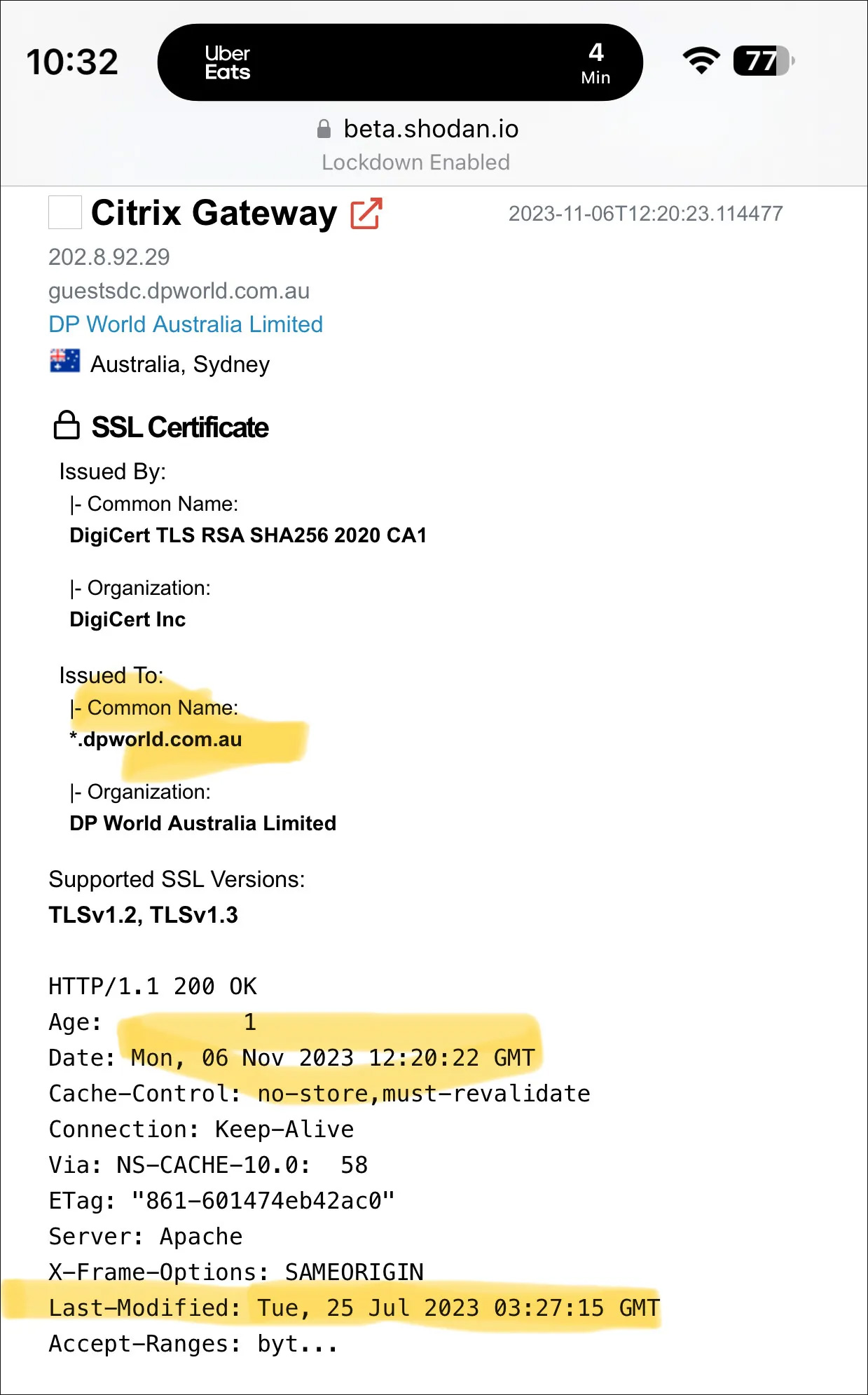
Safety researcher Kevin Beaumont, who has been monitoring the assaults, has discovered that many current victims additionally utilized susceptible Citrix Netscaler gadgets on the time of the assault, permitting preliminary entry to the company community.
Some firms that lately suffered a cyberattack and utilized susceptible Citrix Netscaler gadgets embrace Toyota Monetary Companies, Industrial and Business Financial institution of China (ICBC), DP World, Allen & Overy, and Boeing.
Supply: Kevin Beaumont
Whereas it’s identified that associates for the LockBit and Medusa ransomware gangs are behind a few of these assaults, it’s probably extensively being exploited by different legal operations.
In different information, the BlackCat ransomware gang took the daring step of submitting an SEC grievance on one among its victims for not disclosing they suffered a cyberattack.
The menace actors tried to get the corporate into bother for a brand new SEC rule that requires publicly traded firms to report cyberattacks inside 4 days if they’ve a fabric affect. Nonetheless, this rule doesn’t go into impact till December fifteenth, 2023.
Whereas many ransomware gangs have threatened to report cyberattacks to the SEC if a ransom was not paid, this could possibly be the primary publicly disclosed use of the extortion technique.
We additionally discovered extra about current assaults and ways utilized by ransomware menace actors, that are highlighted under:
Contributors and people who offered new ransomware data and tales this week embrace: @serghei, @demonslay335, @billtoulas, @fwosar, @Seifreed, @malwrhunterteam, @BleepinComputer, @Ionut_Ilascu, @LawrenceAbrams, @GossiTheDog, @BrettCallow, @PogoWasRight, @pcrisk, and @NCCGroupInfosec.
November thirteenth 2023
FBI: Royal ransomware requested 350 victims to pay $275 million
The FBI and CISA revealed in a joint advisory that the Royal ransomware gang has breached the networks of at the least 350 organizations worldwide since September 2022.
Don’t throw a hissy match; defend towards Medusa
To not be confused with MedusaLocker, Medusa was first noticed in 2021, is a Ransomware-as-a-Service (RaaS) usually utilizing the double extortion methodology for financial acquire. In 2023 the teams’ exercise elevated with the launch of the ‘Medusa Weblog’. This platform serves as a software for leaking information belonging to victims.
Key Ransomware Indicator Up 56% 12 months-on-12 months: October Knowledge
In October assaults fell by 15.12% from the prior month in keeping with the amount of victims posted on ransomware leak websites, however remained excessive from a year-on-year perspective with a 54.67% enhance over October 2022. Final month additionally marked the tenth consecutive with a YoY enhance in ransomware victims posted to leak websites, and the eighth consecutive with a depend above 300.
New 1337 Ransomware
PCrisk discovered a brand new 1337 Ransomware that appends the .1337 extension and drops a ransom notice named yourhope.txt.
November 14th 2023
LockBit ransomware exploits Citrix Bleed in assaults, 10K servers uncovered
The Lockbit ransomware assaults use publicly out there exploits for the Citrix Bleed vulnerability (CVE-2023-4966) to breach the techniques of huge organizations, steal information, and encrypt recordsdata.
New GlobeImposter variant
PCrisk discovered a brand new GlobeImposter variant that appends the .Pig865qq extension.
November fifteenth 2023
Ransomware gang recordsdata SEC grievance over sufferer’s undisclosed breach
The ALPHV/BlackCat ransomware operation has taken extortion to a brand new stage by submitting a U.S. Securities and Trade Fee grievance towards one among their alleged victims for not complying with the four-day rule to reveal a cyberattack.
Toronto Public Library confirms information stolen in ransomware assault
The Toronto Public Library (TPL) confirmed that the non-public data of workers, prospects, volunteers, and donors was stolen from a compromised file server throughout an October ransomware assault.
FBI and CISA warn of opportunistic Rhysida ransomware assaults
The FBI and CISA warned at present of Rhysida ransomware gang’s opportunistic assaults focusing on organizations throughout a number of trade sectors.
New ransomware variant
PCrisk discovered a brand new ransomware variant that appends the .shanova extension and drops a ransom notice named read_it.txt.
November sixteenth 2023
FBI shares ways of infamous Scattered Spider hacker collective
The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Safety Company launched an advisory in regards to the evasive menace actor tracked as Scattered Spider, a loosely knit hacking collective that now collaborates with the ALPHV/BlackCat Russian ransomware operation.
Toyota confirms breach after Medusa ransomware threatens to leak information
Toyota Monetary Companies (TFS) has confirmed that it detected unauthorized entry on a few of its techniques in Europe and Africa after Medusa ransomware claimed an assault on the corporate.
New STOP ransomware variants
PCrisk discovered new STOP ransomware variants that append the .eqza and .eqew extensions.
November seventeenth 2023
British Library: Ongoing outage attributable to ransomware assault
The British Library confirmed {that a} ransomware assault is behind a serious outage that’s nonetheless affecting providers throughout a number of places.
Yamaha Motor confirms ransomware assault on Philippines subsidiary
Yamaha Motor’s Philippines motorbike manufacturing subsidiary was hit by a ransomware assault final month, ensuing within the theft and leak of some workers’ private data.
That is it for this week! Hope everybody has a pleasant weekend!
